Resource Search
Resource Search allows you to explore your resources, stacks and projects in detail.
Query syntax
Resource Search supports a rich query language, described below.
Simple queries
The default search behavior is to return resources that match all terms in your query based on their name, URN, stack, or project.
For example, a query like
bucket
will return resources having types like aws:s3/bucket:Bucket or aws:s3/bucketobject:BucketObject. It will also return resources in stacks named “bucket” or projects named “my-cool-bucket”.
Similarly, a query for
production
will return resources to belonging to stacks named “production”. It will also include any resources with “production” anywhere in its name.
A resource will only be returned if it matches all terms in the query. If you search for
foo bar
a resource named “foo” in the “bar” stack will be returned, but a resource only named “bar” will not be returned.
Field queries
The default search behavior is helpful for preliminary exploration but is often too broad for finer analysis. To more precisely control how your queries match resources, you can explicitly limit part or all of your query to match specific fields.
For example, searching name:production will only return resources that include “production” in their logical name.
In general, any column visible in the UI can be queried as a field by taking the lowercase column name and adding a : followed by a query term.
The colon cannot be followed by whitespace.
The complete list of available fields is below.
category
The category the resource belongs to.
Examples:
- category:compute
- category:storage
- category:data
created
The UTC time when the resource was created.
Resources created or modified with CLI versions below 3.60 do not have created set.
Examples:
- created:2023-03-31
- created:2023-03-31T01:02:03.456
- created:[2023-01-01 to 2023-03-31]
- created:>=2023-01-01
custom
Whether the resource is a CustomResource.
Examples: custom:true | custom:false
delete
Whether the resource is marked for deletion in the next update.
Typically indicates a resource that was not cleaned up due to an error.
Examples: delete:true | delete:false
dependency
The URN of another resource this resource explicitly or implicitly depends on.
A resource can have multiple dependencies. When querying, dependency:foo returns resources with any dependency with a URN matching foo.
Examples:
- dependency:access-logs
- dependency:urn:my-org:my-stack::my-app::aws:s3/bucket:Bucket::access-logs
id
The physical name of the resource, as assigned by the resource’s provider. May not be set if the resource is pending creation.
Example: id:my-bucket-d7c2fa0
modified
The UTC time when the resource’s state was last modified during an update, refresh or import.
Stacks modified with CLI versions below 3.60 record this for all resources as the time of the stack operation, regardless of whether the resource was modified. After CLI version 3.60 the resource’s modified time is only updated when the resource’s state is modified.
Examples:
- modified:2023-03-31
- modified:2023-03-31T01:02:03.456
- modified:[2023-01-01 to 2023-03-31]
- modified:>=2023-01-01
name
The logical name of the resource.
Typically the first parameter provided to the resource when it was instantiated.
Example: name:my-bucket
package
The package component of the resource’s type.
This is aws for a resource of type aws:s3/bucket:Bucket. Can be combined with the version field to find resources using specific package versions.
Examples:
- package:aws
- package:aws-native
- package:gcp
- package:pulumi
- package:random
parent.urn
The URN of the resource’s parent, if it has one.
Examples:
- parent.urn:app-production
- parent.urn:urn:myorg:mystack::app::pulumi:pulumi:Stack::app-production
pending
The state of the resource if it is pending.
Typically indicates an operation that was interrupted due to an error, possibly needing manual intervention to resolve.
Allowed values: creating, deleting, updating, reading, importing.
Examples:
- pending:creating
- pending:deleting
- pending:updating
- pending:reading
- pending:importing
project
The project the resource belongs to.
Example: project:my-cool-repo
protected
Whether the resource is protected from deletion.
Examples: protected:true | protected:false
provider.urn
The URN of the resource’s provider.
Examples:
- provider.urn:aws::default_5_21_1
- provider.urn:urn:myorg:mystack::myproject::pulumi:providers:aws::default_5_21_1::86588ad9
stack
The stack the resource belongs to.
Example: stack:my-cool-stack
type
The type of the resource.
Examples:
- type:LogGroup
- type:aws:cloudwatch:LogGroup
- type:aws:cloudwatch/logGroup:LogGroup
urn
The URN of the resource.
Examples:
- urn:my-log-group
- urn:my-org:my-stack::my-project::aws:cloudwatch/logGroup:LogGroup::my-log-group
version
The version of the package used by the resource. This allows you to find resources using specific versions of packages, which is useful for identifying resources that may need updates.
Examples:
- package:awsx version:<2.0
Exact matching
Surrounding terms with "double quotes" produces an exact match query.
Only resources matching the phrase in quotes exactly (including punctuation and whitespace) will be returned.
An exact match can optionally have a field associated with it.
For example, stack:"my-cool-stack".
Negation
Terms can be excluded from results by prefixing them with a -.
For example, -foo will exclude all resources that would normally match a query for foo.
Negation can be applied to exact matches and fields. All of -name:foo, name:-foo, -name:"foo", name:-"foo", and -"foo bar" are all valid and equivalent.
Fields can be repeated for multiple exclusions: -name:foo -name:bar excludes all resources with names matching foo and bar.
Logical combinations
All terms are implicitly combined with a logical AND, but terms can also be combined with OR.
For example, foo OR bar returns resources that would normally match foo as well as resources that would normally match bar.
Precedence is simple left-to-write, so foo bar OR baz is interpreted as (foo AND bar) OR baz. Parentheses are strongly recommended when combining terms with OR to prevent unexpected results. In this case, you can query for foo (bar OR baz) if your intent is to match bar or baz.
Parentheses and OR can be combined with negation, exact matches, and field queries like so:
“S3-bucket” -(stack:prod OR stack:dev) -project:sandbox
Range queries
The created and modified fields can be queried for a range of values with >, >=, <, <=, and [a to b].
The [a to b] form is inclusive on both sides.
For example, resources modified within the first quarter of 2023 (requires CLI 3.XX):
modified:[2023-01-01 to 2023-03-31]
Ranges can also be one-sided. For example, to query everything modified after January 1, 2023:
modified:>=2023-01-01
Property queries
Property search is only available to organizations using Team, Enterprise and Business Critical editions.
If you would like to use it, contact us to upgrade.
Property search allows you to query resources by their inputs and outputs.
A property query is similar to a field query but it is triggered by a leading . followed by a
property path:
.<property path>:<value?>
For example:
.instanceType:t3.large
The specific syntax for property names matches the syntax used elsewhere in Pulumi, for example with ignoreChanges. This makes it possible to refer to property values nested inside arrays or objects, or values with special characters.
For example, to query for a key containing spaces inside of an output object named tags we can write:
.tags[“name containing spaces”]:value
To query properties nested within arrays, the index can be omitted from the property path or [*] can be used. Resources are returned if any element in the array matches. Querying a specific array index (like [0]) is not supported.
An output of {"foo": [{"bar": "baz"]} can be queried with:
.foo[*].bar:baz
Or, equivalently:
.foo.bar:baz
Matching behavior is similar to field queries. Matching is non-exact by default, and surrounding a term with double quotes triggers exact matching.
For example:
A query for
.instanceType:t3will return resources with anyinstanceTypecontaining “t3”.A query for
.instanceType:"t3.large"will return resources with aninstanceTypematching “t3.large” exactly.
In some cases a resource might have outputs that differ from its inputs, or inputs that are not also outputs. Precedence is given to outputs first when querying.
Existence queries
Omitting a value from a field name results in an existence query that returns all resources with a value set for that field.
For example, to find all resources with a team defined, regardless of what that team is, you can write:
team:
Existence queries can be combined with negation to achieve non-existence queries. These can also be combined with properties.
For example, you would normally write something like .tags.stack:production to find resources with an output like {"tags": {"stack": "production"}}, but we can also find resources with any tags:
.tags:
If we want to refine this to resources with some tags but no "stack" tag specifically, we can can write a query like so:
.tags: -.tags.stack:
Existence queries do not return resources where the property is an empty object ({}), array ([]), or null. A resource with an output of {"tags": {}} would not be captured by an existence query for .tags:.
Resource search grouping
The Row Groups Header allows you to drag columns from the table into the grouping area to organize resources by that column. You can group by multiple columns simultaneously to create a structured view of your resources.
Using the row groups header
Example: Grouping by stack and modified Date
For example, if you want to see resources categorized by stack and last modified date, you can:
- Drag the Stack column into the Row Groups Header.
- Drag the Modified column next to it.
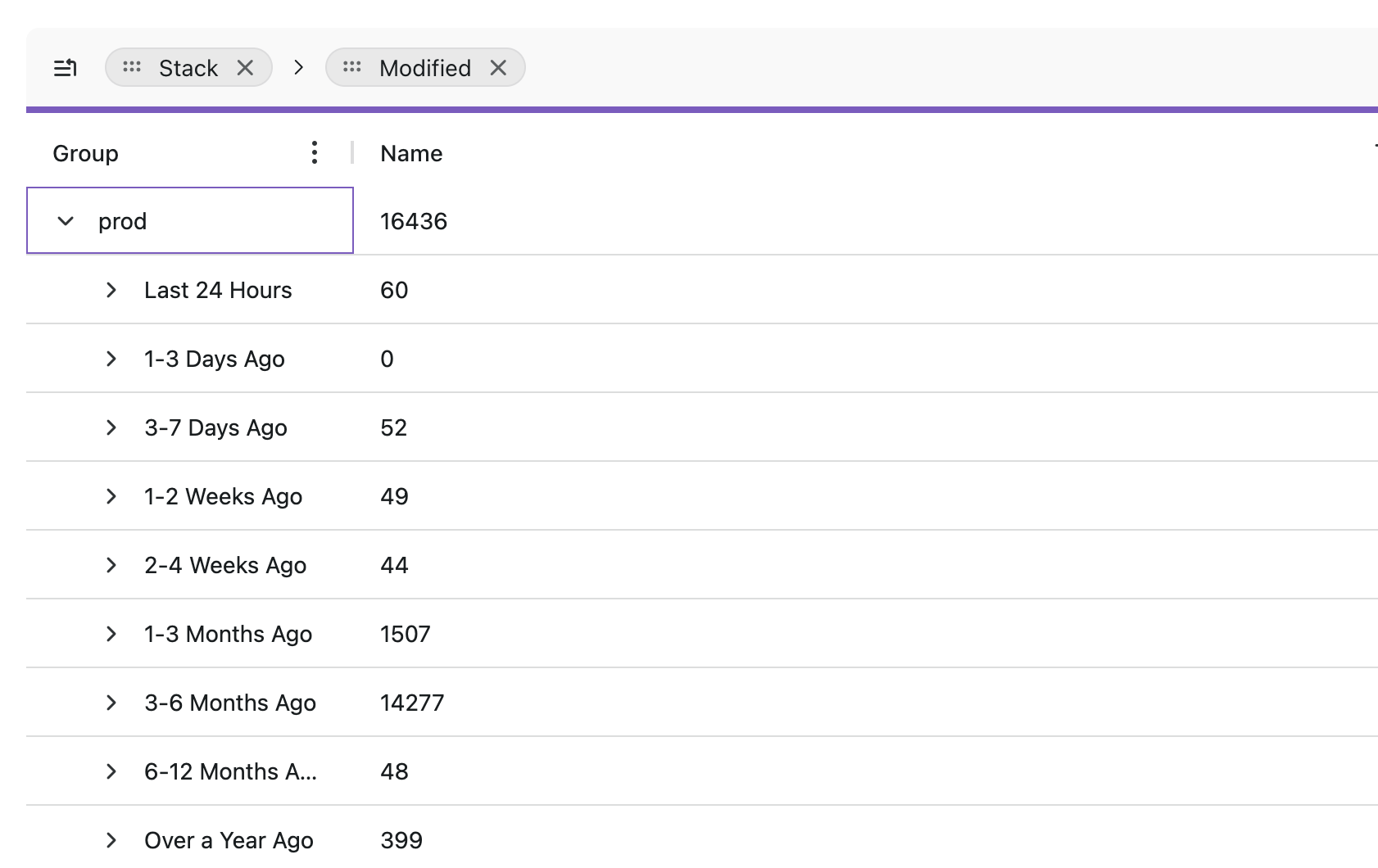
This will create a hierarchical breakdown where:
- Resources are first grouped by stack.
- Within each stack, resources are further grouped by the last modified date.
This allows you to quickly identify which stacks have been recently modified and which resources belong to each stack.
Grouping multiple attributes
You can group by any combination of attributes to match your workflow. Some useful groupings include:
- By Managed By and Stack: To see which resources are managed by Pulumi, discovered, or untracked within each stack.
- By Resource Type and Provider: To analyze resource distribution across cloud providers.
- By Account and Region: To organize resources by cloud accounts and deployment regions.
Selecting the “X” in the filter bar will remove all previously selected filters.
Unified resources
When a resource exists in multiple sources (such as both IaC stacks and Insights scans), Pulumi Cloud consolidates these in the search results. Resources from multiple sources are indicated with a icon in the results table. This behavior helps reduce duplicate entries while ensuring all sources that match your query are considered.
When using the “group by” functionality, a consolidated resource can appear in multiple groups if it has sources present in each group. For example, when grouping by project, a resource that exists in both an IaC stack and an Insights scan from different projects will appear under both project groups.
Managed by attribute
The Resources page in Pulumi Cloud now includes a Managed By column, which helps categorize resources based on how they are managed. This column provides insight into whether a resource is defined by Infrastructure as Code (IaC) using Pulumi or discovered by Pulumi’s resource discovery engine.
Viewing managed by categories
The managed by column classifies resources into two categories:
- Pulumi – Resources provisioned and tracked through Pulumi stacks.
- Other – Resources that were detected by Pulumi’s scanning engine but are not managed by any Pulumi stack.
Column filtering
Expanding the “Column Filter” menu shows you the set of values found for that column along with a count for each value. You can then select a specific value or collection of values to filter your result set.
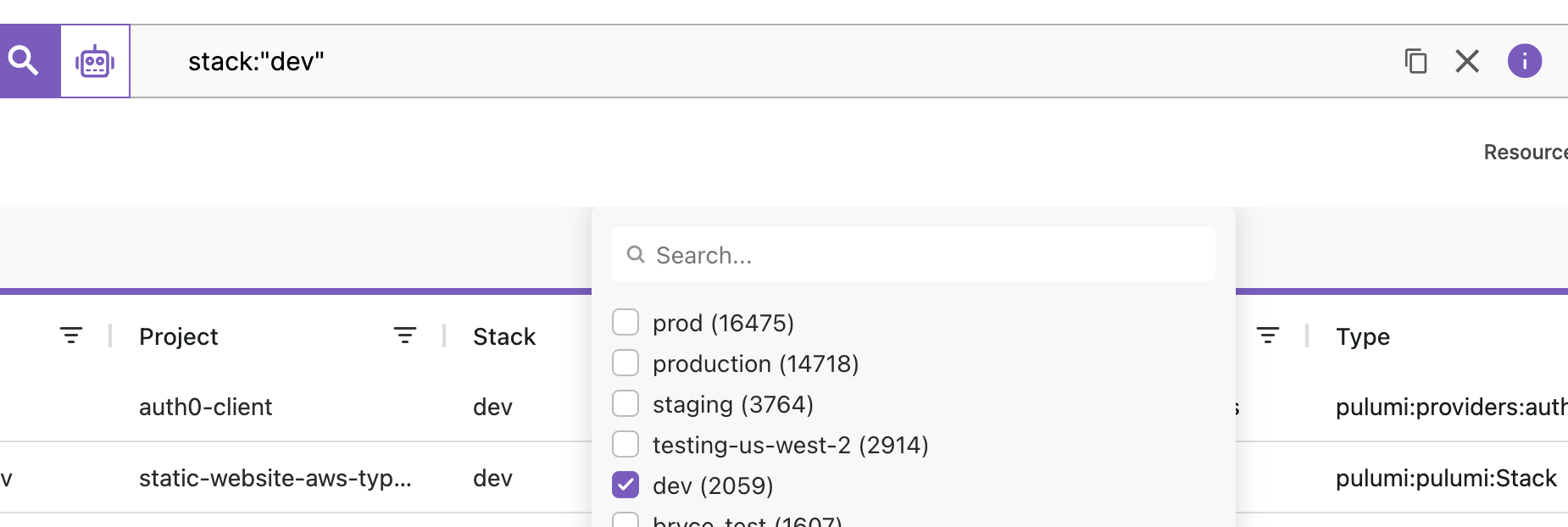
In the example above, the query has been restricted to the “dev” stack.
Clicking the “X” within the search bar will remove all previously selected filters.
Download a CSV
The CSV Export feature is only available to organizations using the Enterprise and Business Critical editions.
If you don’t see it in your organization, contact us.
You can download a CSV with all resources matching your query by clicking the “Export CSV” button within dropdown opened by clicking the gear icon.
For a complete description of the CSV format returned, see the Data Export documentation.
API access
Resources can also be queried programmatically. See the Pulumi Cloud REST API for full details of the API endpoint to query resources.
AI assist
Organizations with AI Assist enabled will see an “AI Assist” button to the right of their search bar.
After clicking “AI Assist” you can input a natural language query, for example:
How many VPCs do I have?
You will then be re-directed to the “Syntax” tab with a pre-populated search query that attempts to answer your question. The search bar will remain empty if it’s not able to generate a valid query for your question.
You may need to refine the pre-populated query slightly to capture your intent. For example, if you ask, “How many buckets do I have?” it might give you a query like
type:“aws:s3/bucket:Bucket”
This isn’t accurate if you’re using Google Cloud, however. In that case you could modify the query to be
type:“gcp:storage:Bucket”
or, if you’re not sure which type is appropriate, you can use AI Assist again to clarify:
How many gcp buckets do I have?
You may want to expand the “Advanced filtering” menu if you are interested in specific resource counts.
You do not need to query AI Assist with English:
(type:aws:ec2/instance:Instance OR type:azure:compute:VirtualMachine OR type:gcp:compute:Instance)
Access controls
Resource Search is available to all members of an organization, but as a user you are only able to see and query resources that you have permission to access. More specifically:
Thank you for your feedback!
If you have a question about how to use Pulumi, reach out in Community Slack.
Open an issue on GitHub to report a problem or suggest an improvement.