CIS Compliance for Azure
CIS Compliance for Azure
CIS compliance is crucial for establishing strong security controls and safeguarding your cloud infrastructure against cyber threats. Pulumi can help you identify existing cloud resources that are not in compliance, and it can also enforce compliance policies proactively before infrastructure is deployed. Get started with Pulumi to use these compliance tools or speak with a Solutions Architect to get an expert consultation.
What is CIS Compliance?
CIS (Center for Internet Security) Compliance refers to the adherence to security best practices outlined by the CIS, a nonprofit organization that develops globally recognized security standards. These best practices are known as CIS Controls and CIS Benchmarks, which provide guidelines for securing various technologies and systems, including operating systems, cloud services, network devices, and software.
Key Aspects of CIS Compliance
- Implementation of Controls: Start by implementing the CIS Controls relevant to your organization's size and risk profile.
- Use CIS Benchmarks: Configure your systems and applications according to CIS Benchmarks.
- Regular Audits: Continuously monitor and audit your systems to ensure ongoing compliance with CIS recommendations.
- Automation Tools: Consider using CIS-CAT (CIS Configuration Assessment Tool) or other automation tools to assess and enforce compliance across your infrastructure.
Benefits of CIS Compliance
- Standardized Security: Ensures that your organization follows industry-recognized security best practices.
- Risk Reduction: Helps in reducing the attack surface by implementing critical security controls.
- Compliance with Other Standards: CIS Controls and Benchmarks often overlap with other compliance frameworks like PCI-DSS, NIST, and ISO, making it easier to achieve multiple compliance goals simultaneously.
- Improved Incident Response: By implementing CIS Controls, organizations are better equipped to detect, respond to, and recover from security incidents.
CIS Compliance for your Azure Infrastructure
1. Identity and Access Management (Azure AD)
- Root Account Protection: Ensure that the Azure subscription's root account (Global Administrator) is not used for everyday tasks and that Multi-Factor Authentication (MFA) is enabled for this account.
- Role-Based Access Control (RBAC) Policies: Apply the principle of least privilege by ensuring that RBAC roles grant the minimum permissions required for users, groups, and services.
- MFA for Azure AD Users: Require MFA for all Azure AD users with Azure portal access.
- Password Policies: Implement strong password policies in Azure AD, including complexity requirements, password expiration, and self-service password reset options.
2. Logging and Monitoring
- Azure Activity Logs: Enable Azure Activity Logs across all regions to record all management-level operations on your resources. Ensure logs are archived in Azure Storage with encryption and immutability for added security.
- Azure Monitor: Set up Azure Monitor to track key metrics and create alerts for unusual activities, resource utilization, or threshold breaches.
- NSG Flow Logs: Enable Network Security Group (NSG) Flow Logs to capture information about IP traffic to and from resources within your Virtual Network (VNet).
3. Networking
- NSGs and ASGs: Ensure that your Network Security Groups (NSGs) and Application Security Groups (ASGs) are configured to allow only necessary traffic. Regularly review and restrict inbound and outbound rules.
- Public Access to Resources: Avoid public access to sensitive resources. Ensure that no NSGs or Public IP addresses allow unrestricted access (e.g., 0.0.0.0/0) unless explicitly required and properly monitored.
- Jumpbox VMs: Use Jumpbox Virtual Machines (VMs) for secure SSH or RDP access to resources. These should be the only publicly accessible VMs and tightly controlled.
4. Encryption
- Azure Storage Encryption: Ensure that all Azure Storage accounts (Blob, File, Table, Queue) use server-side encryption (SSE) to protect data at rest. Enable default encryption for all new storage accounts.
- Azure SQL Database and Managed Disk Encryption: Enable encryption for Azure SQL Databases and Azure Managed Disks, including data at rest, backups, and transparent data encryption (TDE).
- Azure Key Vault: Use Azure Key Vault to manage and rotate encryption keys. Ensure that access to Key Vault keys is restricted through RBAC and monitored with audit logs.
5. Auditing and Assessment Tools
- Azure Policy: Use Azure Policy to assess, audit, and enforce the configuration of your Azure resources. Set up compliance policies that align with CIS Benchmarks and trigger alerts for non-compliance.
- Azure Security Center: Enable Azure Security Center to aggregate security findings, compare them against best practices, and offer recommendations. Security Center also helps monitor compliance and generate reports.
- CIS-CAT Tool: Use the CIS Configuration Assessment Tool (CIS-CAT) to automate the assessment of your Azure environment against the CIS Benchmarks.
6. Automation and Continuous Compliance
- Infrastructure as Code (IaC): Use tools like Pulumi to define your infrastructure as code. This ensures that CIS-compliant configurations are applied consistently and efficiently across environments.
- Automated Remediation: Implement automated remediation for non-compliant resources using Azure Automation or Azure Policy to enforce continuous compliance.
- Continuous Monitoring: Regularly monitor your environment with tools like Azure Monitor, Azure Policy, and Azure Sentinel to ensure ongoing compliance with CIS benchmarks.
7. Documentation and Reporting
- Compliance Documentation: Maintain up-to-date documentation of your CIS compliance efforts, including policies, configurations, and monitoring setups in your Azure DevOps or documentation repositories.
- Regular Audits: Schedule regular internal audits using Azure Compliance Manager to review configurations against the CIS benchmarks and update them as necessary.
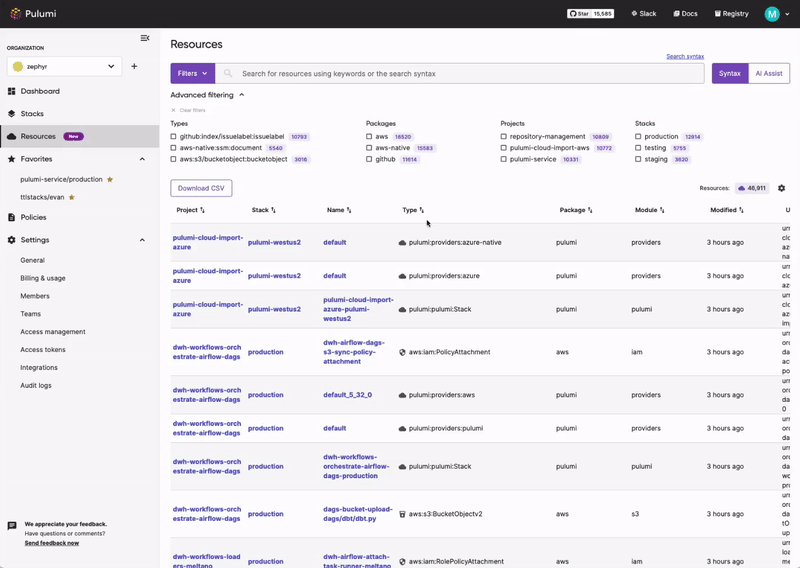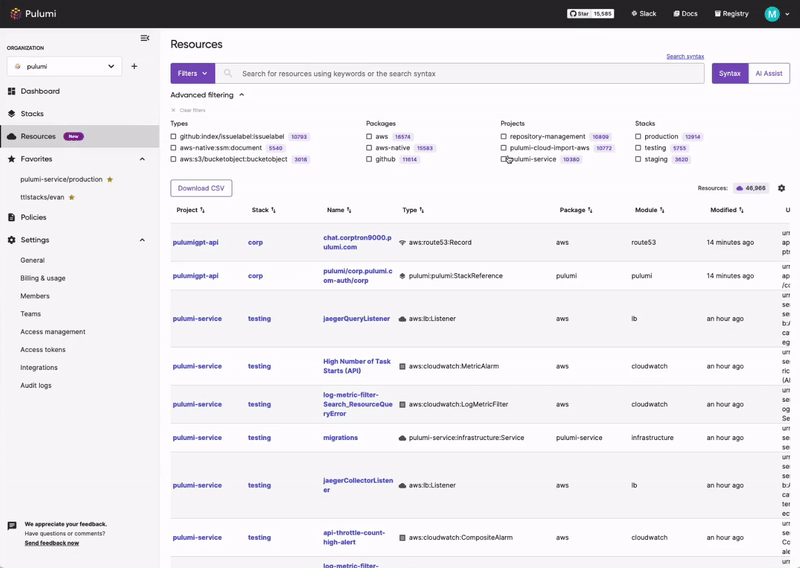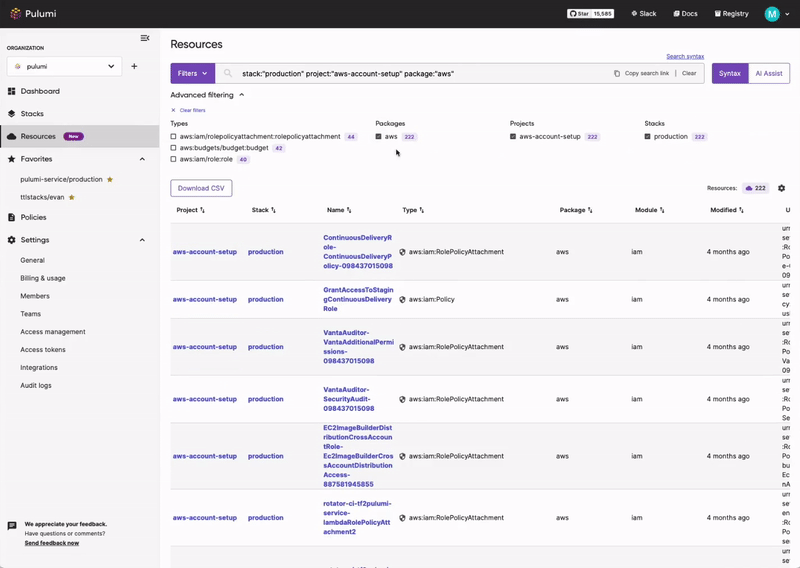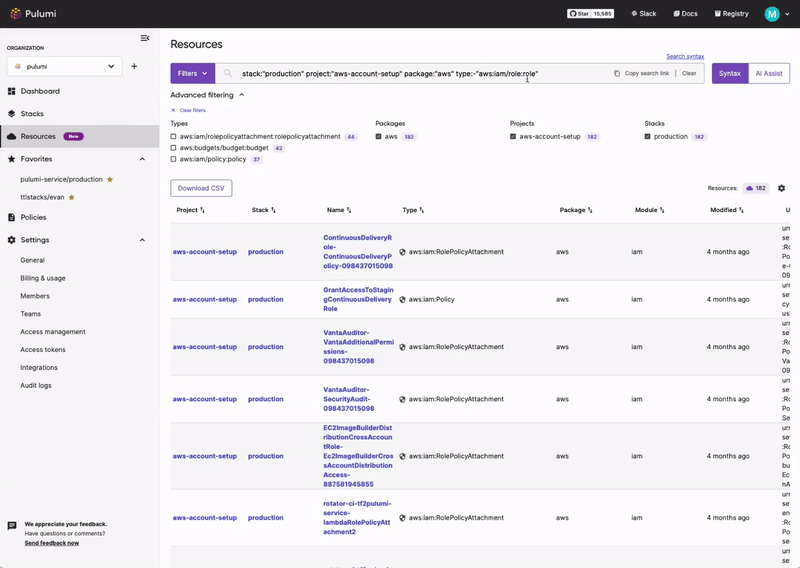
Pulumi Insights
Use Pulumi Insights to gain visibility into your cloud infrastructure's configuration to assess CIS compliance. Pulumi Insights is Intelligent Cloud Management. It helps you gain security, compliance, and cost insights into the entirety of your organization's cloud assets and automatically remediate issues.
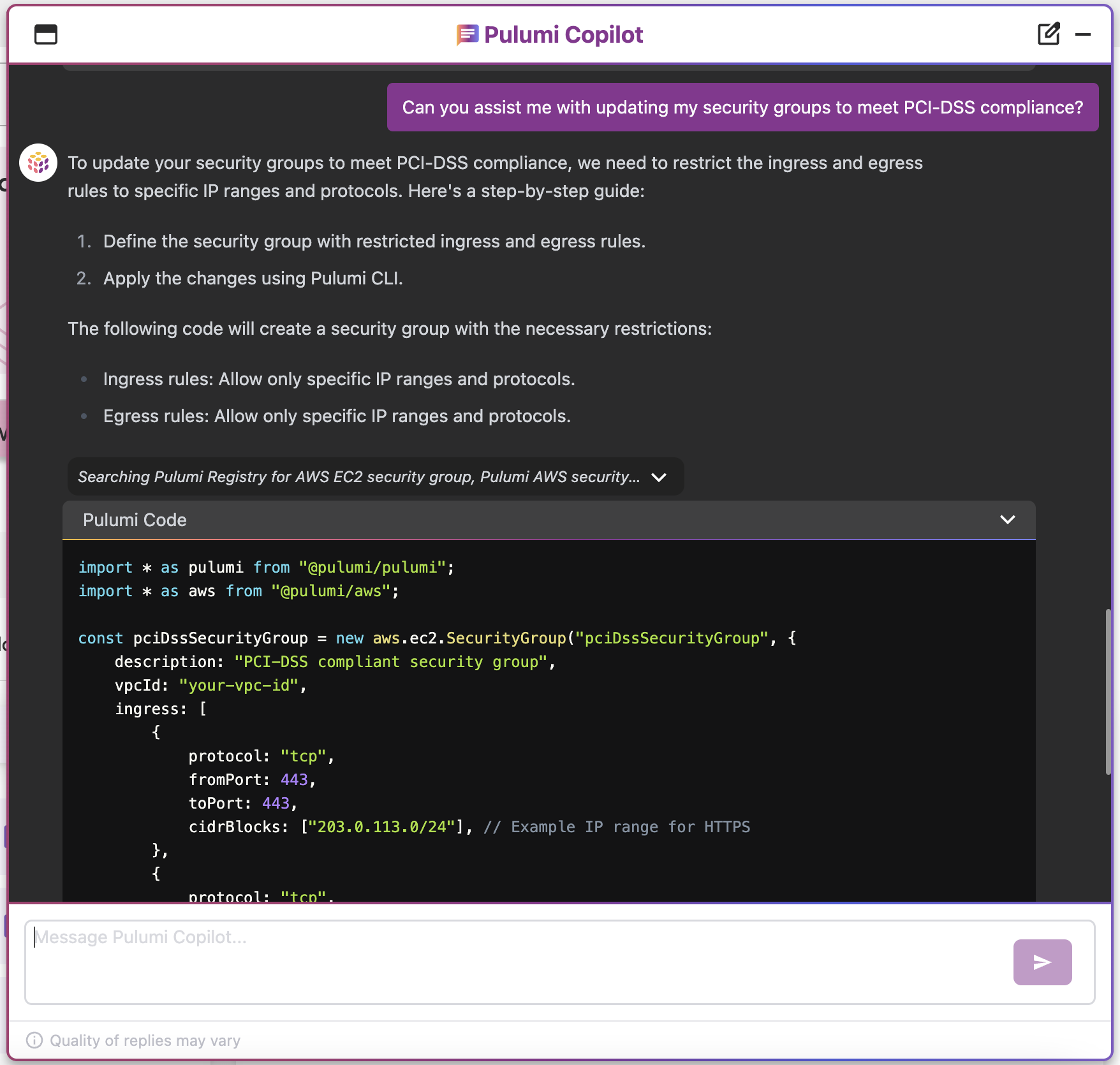
Pulumi Copilot
Use Pulumi Copilot to assist configuring your infrastructure to make it compliance ready. You can tap into the Pulumi Copilot's deep understanding of your organization's context to gain visibility into the configuration of resources and assess their compliance.
Compliance Ready Policies
With comprehensive coverage of Azure, Pulumi Compliance Ready Policies provide an enhanced level of control and governance over your cloud resources. Pulumi Compliance Ready Policies empower you to enforce best practices, security standards, cost controls, and compliance requirements seamlessly within your infrastructure-as-code workflows.
Compliance for Azure Services
Learn more about how Pulumi can make your Azure services CIS compliant.
Talk to a Solutions Architect
Get in touch with our Solutions Architects to get all your resources in use with Pulumi Insights