Pulumi CrossGuard
Enforce your organization's cloud governance — security, compliance, cost controls, and more.
Features
Any Policy
Use off-the-shelf rules or define your own for security, cost, compliance, reliability best practices — just about anything. Use package managers to share and reuse rules.
Any Cloud
Govern application and infrastructure resources on any cloud, including AWS, Azure, Google Cloud, Kubernetes, and 150+ more infrastructure providers.
Familiar and Powerful
Define custom policies using familiar languages like JavaScript and Python. Use great editors, test frameworks, libraries, and tools for productivity and correctness.
Flexible Enforcement
Apply policies using coarse- or fine-grained controls. Target individual projects, manage organization-wide policies, or group projects for differences in environments and regions.
Configurable
Define policies that can be configured at the point of application, including enforcement level, letting you vary behavior based on project needs.
Automate and Integrate
Automate governance using programmable libraries and REST APIs, easily integrating with external services such as web services, asset tracking databases, pricing lists, and more.
Enterprise Compliance Enforcement
Compliance-ready Policies
Choose from hundreds of policies for AWS, Azure, Google Cloud, and Kubernetes. Support for PCI DSS, ISO 27001, SOC 2, and CIS Benchmarks.
Server-side Enforcement
Set policy packs that block prohibited deployments across your entire organization, preventing issues.
Remediation Policies
Codify reactive solutions to compliance requirements by transforming non-compliant resources into compliant ones.
Policy as Code Scenarios
Accelerate your organization's delivery while still staying compliant
Security
Maintain security across all cloud infrastructure assets.
new PolicyPack("acmecorp-security", {
policies: [{
name: "prohibited-public-internet",
description: "Reject public internet access.",
enforcementLevel: "mandatory",
validateResource: validateResourceOfType(
aws.ec2.SecurityGroup,
(sg, args, reportViolation) => {
const hasInternetAccess = sg.ingress.find(
rule => rule.cidrBlocks.includes("0.0.0.0/0")
);
if (hasInternetAccess) {
reportViolation("Illegal internet access");
}
},
),
}],
);Prohibiting network access from the Internet.
Compliance
Meet, and stay meeting, compliance standards.
new PolicyPack("acmecorp-compliance", {
policies: [{
name: "required-storage-region",
description: "Data must be stored in the US.",
enforcementLevel: "mandatory",
validateResource: validateResourceOfType(
aws.s3.Bucket, (bucket, args, reportViolation) => {
if (!bucket.region.startsWith("us-")) {
reportViolation("Non-US bucket detected");
}
},
),
}],
);Disallowing storage outside of specific regions.
Cost Controls
Ensure cost conscious deployments.
new PolicyPack("acmecorp-cost", {
policies: [{
name: "required-cost-tags",
description: "Cost tags are required.",
enforcementLevel: "mandatory",
validateResource: (args, reportViolation) => {
if (isTaggable(args.type) &&
!args.resource["tags"]["Cost Center"]) {
reportViolation("Resource missing tags");
}
),
}],
);Requiring specific cost allocation tags.
Continuous Delivery
Catch policy violations before they escape using CI/CD.
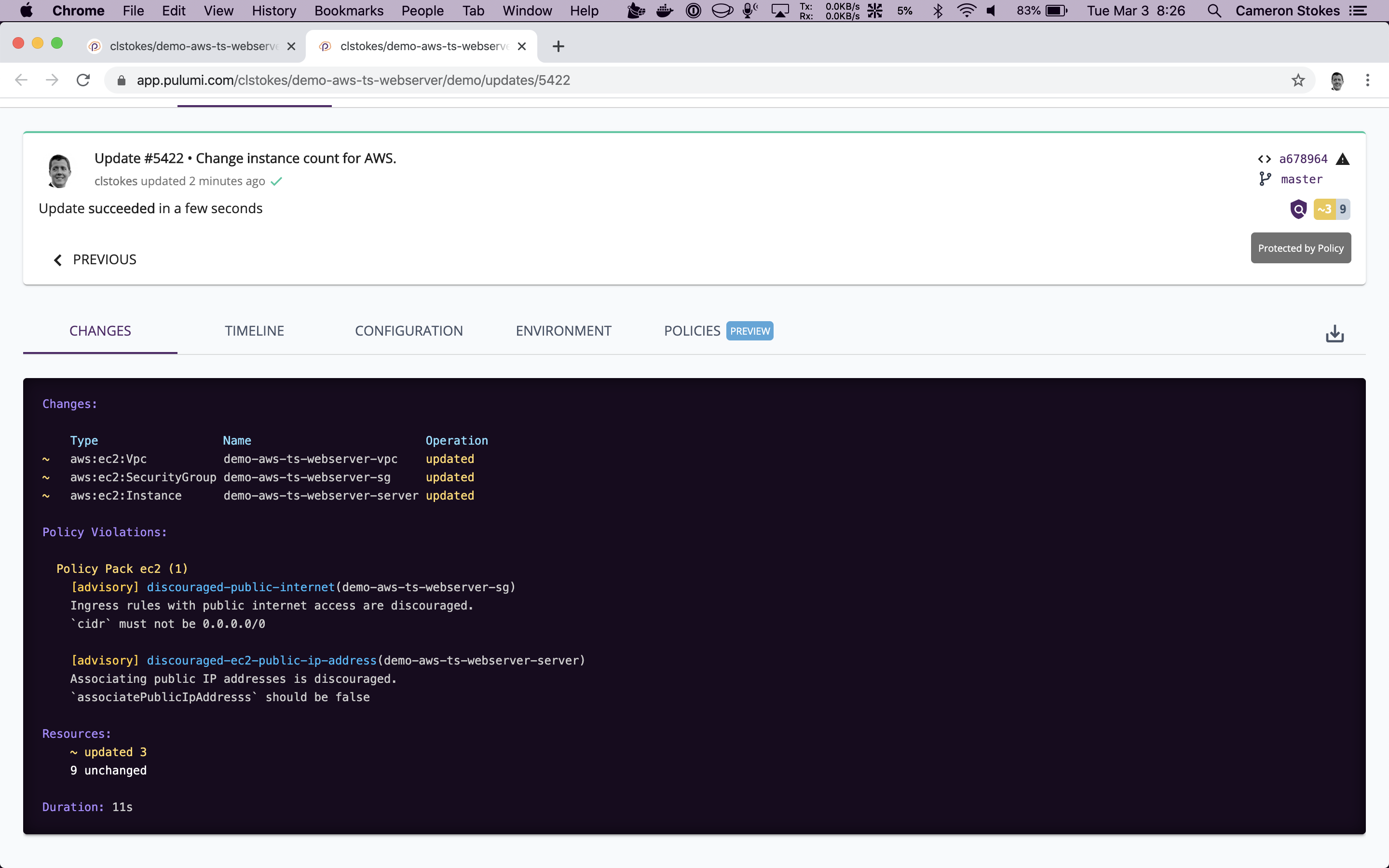
A live dashboard of organizational violations in Pulumi Cloud.
Pulumi supercharged our whole organization by letting us create reusable building blocks that developers can leverage to provision new resources and enforce organizational policies for logging, permissions, resource tagging and security. This has empowered our developer teams to self-provision resources and ship new capabilities faster without having to wait for the infrastructure team to deploy new resources on their behalf.
Igor Shapiro
Principal Engineer
CrossGuard gives us the ability to prevent undesired and insecure resources from being deployed to any environment. It also allows us to block the deployment of certain resource SKUs that may incur unnecessary expense.
Dennis Sauvé
DevOps Engineer
With Pulumi CrossGuard we can provide reusable infrastructure components to our application teams and ensure that their implementations adhere to company standards.
Fernando Carlietti
Lead DevOps Engineer