Intelligent Infrastructure Management
Pulumi Cloud is the smartest and easiest way to automate, secure, and manage everything you run in the cloud. It stores infrastructure state, centralizes secrets management, provides search and clear visibility into all your clouds, runs remote deployments, integrates with CI/CD pipelines, and enforces security and compliance policies.
✨ New - Pulumi Insights 2.0 - Import and Sync All Cloud Infrastructure: Get started now ✨
Products
Pulumi IaC

-
Pulumi Cloud is a fully managed service for infrastructure as code. Store your infrastructure’s state for any cloud in Pulumi’s secure backend, which has built-in scaling, availability, and fault tolerance. You also get access to granular access controls, CICD integrations, SAML/SCIM, audit logging, and more.
Allow developers to safely deploy in parallel with concurrent state-locking.
Audit changes or rollback to previous versions with a complete history of your state.
-
Use built-in secrets management for encrypted data such as credentials or tokens. Store and manage collections of config in Pulumi ESC into environment groupings.
Your infrastructure state is encrypted in transit and at rest.
Sensitive configurations (e.g. database passwords, cloud tokens) are stored as secrets.
Use Pulumi’s secrets manager or integrate with AWS KMS, Azure Key Vault, Google KMS, and HashiCorp Vault.
-
With Automation API, you can use the Pulumi engine as a strongly typed SDK in your application code, enabling it to call functions that can provision and configure infrastructure on any cloud.
Automation API enables you to build custom cloud interfaces for your technical end users. For example, build self-service developer portals, CLIs, frameworks, and CI/CD workflows.
Easily build high-scale, SaaS applications that serve customers with single-tenant instances. Automate creating and managing infrastructure for thousands of unique customers.
-
Integrate Pulumi with your software delivery pipeline so that you can version, build, test, and deploy infrastructure code like software.
Work with existing tools like IDEs, test frameworks, and package managers.
Integrate your source control system so teams can trace changes back to commits and pull requests.
Continuously deliver infrastructure through existing pipelines with CI/CD integrations.
Use event-based webhooks to notify external services like Slack or continuous integration tools.
Use the Service API to manage stacks, updates, teams, and more.
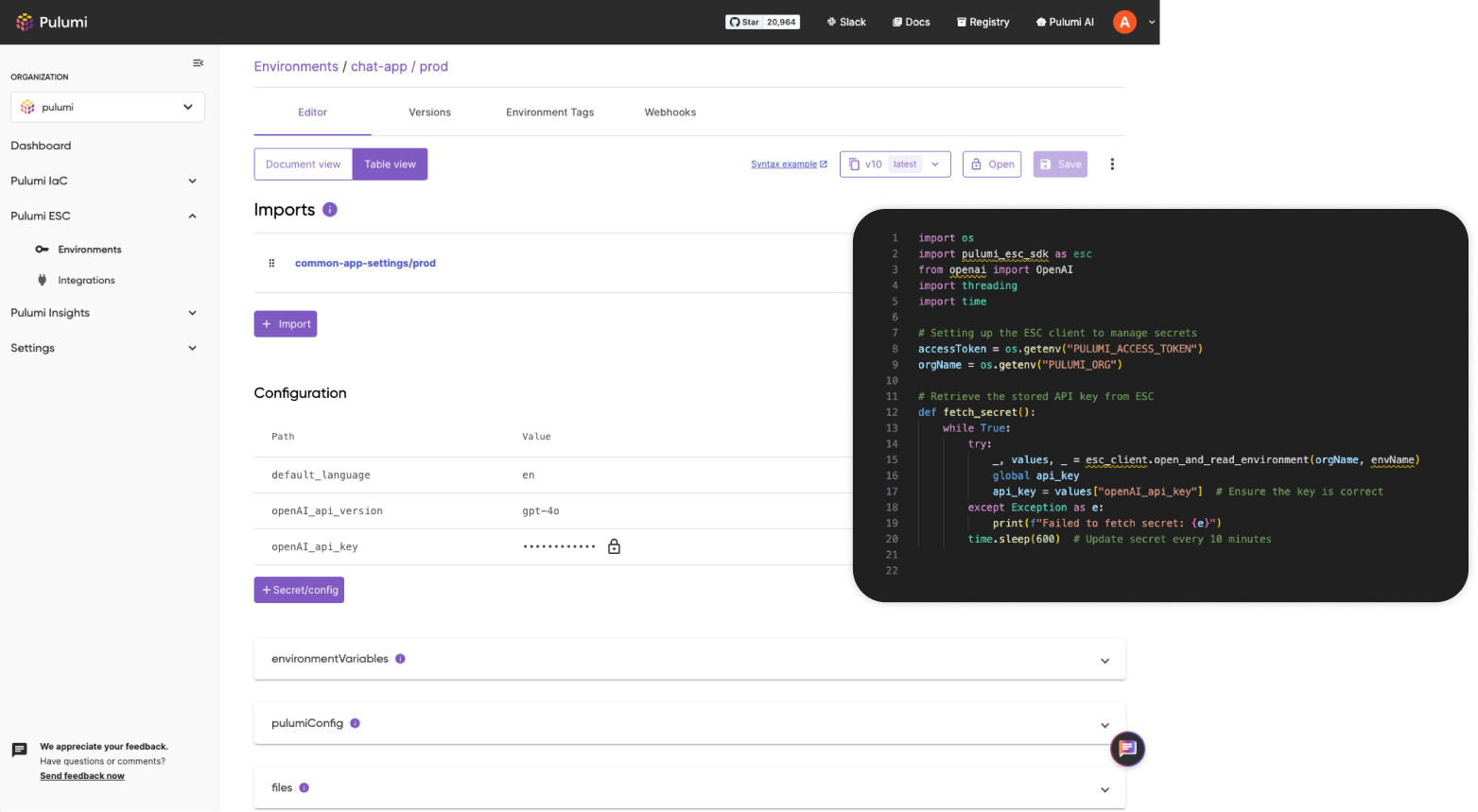
Pulumi ESC
-
Pull and sync configuration and secrets with any secrets store – including HashiCorp Vault, AWS Secrets Manager, Azure Key Vault, GCP Secret Manager, 1Password, and more – and consume in any application, tool, or CI/CD platform.
Access, share, and manage confidential information such as secrets, passwords, and API keys as well as configuration information such as network settings and deployment options.
Environments support importing one into another, allowing for easy composability and inheritance of shared secrets and configuration.
Every change to an environment as well as any of its secrets and configuration is versioned, so rolling back or accessing an old version is easy.
-
Every environment can be locked down with role-based access controls (RBAC) and versioned with all changes fully logged for auditing.
Pulumi ESC leverages the same Pulumi Cloud identity, RBAC, Teams, SAML/SCIM, OIDC, and scoped access tokens used for Pulumi IaC to ensure secrets management complies with enterprise security policies.
Every time secrets or configuration values are accessed or changed with Pulumi ESC, the action is fully logged for auditing. Logs include who accessed what, the action they took, and even a full record of showing which originating environments accessed values are inherited from.
-
No more storing secrets in plaintext on dev computers. Developers can easily access secrets via CLI, API, Kubernetes operator, the Pulumi Cloud UI, and in-code with Typescript/Javascript, Python, and Go SDKs.
Pulumi ESC also provides just-in-time, short-lived credentials, making them easy to adopt as a security best practice.
-
Use Pulumi ESC to centrally manage your configuration and secrets independently of Pulumi IaC, or use ESC and IaC together for the convenience of storing secrets in config with a higher degree of security than using plaintext.
Developers can easily access secrets via CLI, API, Kubernetes operator, the Pulumi Cloud UI, and in-code with Typescript/Javascript, Python, and Go SDKs.
Pulumi Insights

-
View resources deployed in all your clouds, organized in projects and stacks, so that you know what’s running and where.
View dashboards for quick insights into your infrastructure, such as how many resources are running and who has made changes.
Tag stacks for easier filtering and searching.
Jump directly to the cloud console for each resource you’ve deployed with Pulumi.
-
Easily look for resources in a single cloud or across all your clouds with structured queries or natural language search.
Search for resources by filtering with facets like type, provider, project, and stack.
Use a structured query syntax or natural language search (coming soon).
Share queries with your teammates.
Cross-Product Capabilities
Pulumi CrossGuard

-
Set guardrails for developers deploying with Pulumi by creating policy packs that enforce your deployment rules.
Define Policy as Code rules for security, best practices, and more.
Assign policy packs that run on specific stacks (e.g., dev/test/staging rules).
Automatically block deployments that violate your organization’s policies.
-
Business Critical customers can enforce compliance and remediate non-compliance using Pulumi provided policies across your organization.
Choose from hundreds of policies for AWS, Azure, Google Cloud, and Kubernetes. Support for PCI DSS, ISO 27001, SOC 2, and CIS Benchmarks.
Set policy packs that block prohibited deployments across your entire organization, preventing issues.
-
Policies can remediate violations to fix the problems found in addition to reporting them as violations.
Here are a few examples of the remediation policy use cases:
- Tagging resources with standard, organization-wide tags.
- Disabling Internet access for gateways and firewall rules.
- Enabling encryption on storage or buckets.
- Down-sizing virtual machine configuration to use less expensive machine types.
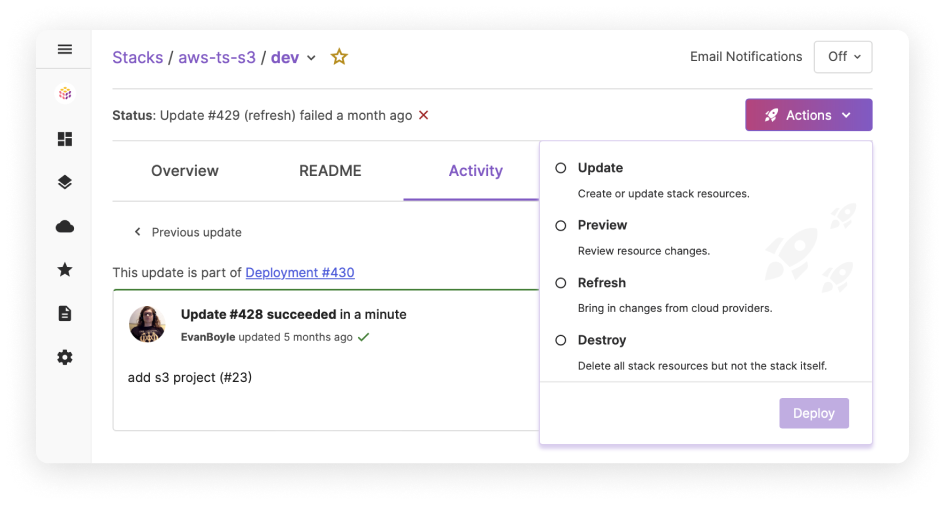
Pulumi Deployments
-
Run remote infrastructure commands to provision, configure, and destroy cloud resources, all executed in a secure cloud environment.
Trigger deployments via REST API, click to deploy from Pulumi Cloud’s console, Git Push to Deploy, Remote Automation API, and other programmatic building blocks.
Use a simple, centralized format for specifying everything needed to deploy your infrastructure stacks.
-
Use the Pulumi Deployments REST API to programmatically trigger deployments for high volume infrastructure automation use cases.
Call Pulumi’s REST API endpoint to trigger Pulumi commands that run in Pulumi Cloud (e.g., update, destroy, refresh, preview).
Offload your local Automation API deployment workloads to Pulumi Cloud via the Remote Automation API feature.
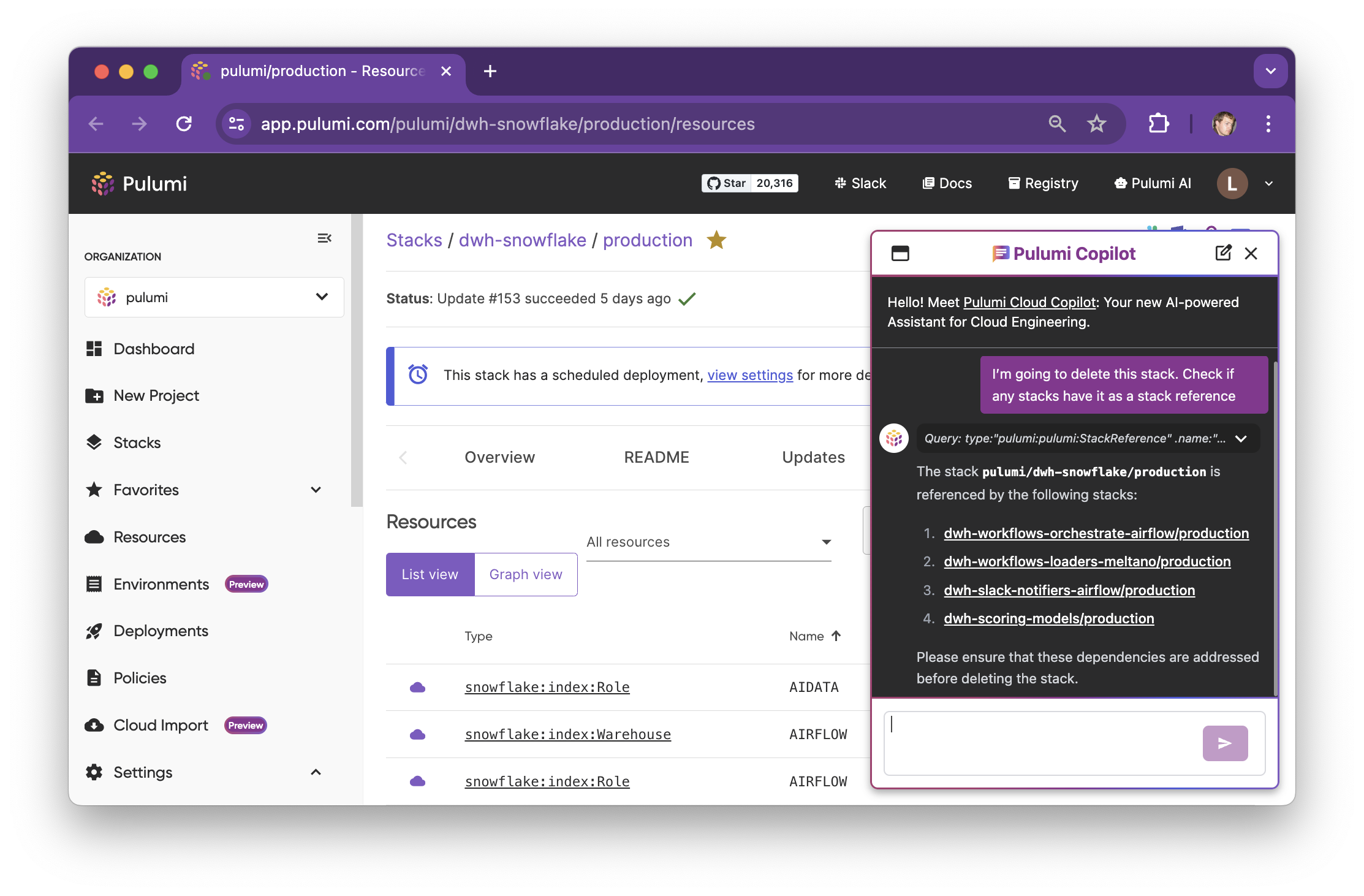
Pulumi Copilot
-
Generate a Pulumi program and deploy cloud infrastructure in seconds with a few simple text prompts.
Example Pulumi Copilot prompts:
“Create a new serverless application on AWS”
“Configure a Kubernetes cluster with best practices on Azure”
“Deploy a Cloudflare worker that uses sticky load balancing to distribute traffic to my Google Cloud backend”
-
Pulumi Copilot has access to all of your Pulumi projects and stacks, and can relate those to your live cloud environments.
Example Pulumi Copilot prompts:
“What versions of Kubernetes do I currently have deployed?”
“What AWS account does VPC vpc-04a11 live within?”
“What environments do we have related to Azure?”
“Describe the architecture of my www-frontend project.”
-
Pulumi Copilot uses a combination of Pulumi and cloud understanding to discover and reclaim cloud waste.
Example Pulumi Copilot prompts:
“What are my least used, most expensive resources?”
“What are my top 10 most expensive cloud resources?”
“How much did my cloud costs increase month over month – and what team was responsible for driving them upwards?”
-
Pulumi Copilot leverages knowledge about security best practices by combining Pulumi’s supergraph and cloud skills.
Example Pulumi Copilot prompts:
“Do I have any insecure endpoints open to the Internet?”
“Do any of my S3 buckets have public-read access? If yes, help me make them private.”
“Do you see any anomalous activity within the past 48 hours?”
-
Pulumi Copilot can access history, logs, and runtime metrics so you can easily get answers about what is failing and why.
Example Pulumi Copilot prompts:
“Why did my deployment yesterday fail?”
“We had an outage Thursday evening around 11pm. Do you understand why?”
“I can’t access my EC2 instance i-3f8e over the Internet, why?”
Team Management
-
Integrate SSO and your identity provider with Pulumi, set user permissions for each stack, and track user activity with audit logs.
Single sign-on with any SAML 2.0 identity provider like Azure Active Directory, Google Workspace , Okta, and OneLogin.
Manage Pulumi access from your central identity provider via SCIM 2.0 integration.
Set role-based access controls that limit who can access infrastructure.
Track the activity of users within your organization with audit logs.
-
Add teammates to Pulumi so you can work on projects together, ship code collaboratively, and coordinate changes to infrastructure.
Invite new team members and share projects to collaborate on infrastructure.
View timelines that show diffs of changed resources and who made the changes.
Tag stacks for easier filtering and searching.
The easiest way to use Pulumi open source
Pulumi Cloud is a managed service for Pulumi IaC’s open source CLI and SDK. It tracks your infrastructure’s state and coordinates updates with the CLI, which creates or updates resources to reach your infrastructure’s desired state.
You can also use any cloud or on-premises storage to build and run your own backend.

Pulumi takes security seriously
Pulumi Cloud runs in an AWS VPC and our architecture follows industry best practices. All network communication is encrypted using TLS and Pulumi’s endpoints are only accessible via HTTPS. Your data is also encrypted at-rest and Pulumi is compliant with SOC 2 Type II.

Customers innovating with Pulumi Cloud
Starburst
Increased velocity and speed, with deployments that are up to 3x faster.
Snowflake
Built a multi-cloud, Kubernetes-based platform to standardize all deployments
Deployment options
SaaS
Use Pulumi Cloud without worrying about scaling, availability, fault tolerance, and concurrency.
Pricing
Pulumi Cloud offers Editions for Individual, Team, Enterprise, and Business Critical. Support is available on Enterprise and Business Critical. You only pay for what you use, and there are free tiers available.
Get started today
Get started today
Pulumi is open source and free to get started. Deploy your first stack today.