Achieve CIS Compliance for Google Cloud Compute Engine
Achieve CIS Compliance for Google Cloud Compute Engine
CIS compliance is crucial for establishing strong security controls and safeguarding your cloud infrastructure against cyber threats. Pulumi can help you identify existing cloud resources that are not in compliance, and it can also enforce compliance policies proactively before infrastructure is deployed. Get started with Pulumi to use these compliance tools or speak with a Solutions Architect to get an expert consultation.
What is CIS Compliance?
CIS (Center for Internet Security) Compliance refers to the adherence to security best practices outlined by the CIS, a nonprofit organization that develops globally recognized security standards. These best practices are known as CIS Controls and CIS Benchmarks, which provide guidelines for securing various technologies and systems, including operating systems, cloud services, network devices, and software.
Key Aspects of CIS Compliance
- Implementation of Controls: Start by implementing the CIS Controls relevant to your organization's size and risk profile.
- Use CIS Benchmarks: Configure your systems and applications according to CIS Benchmarks.
- Regular Audits: Continuously monitor and audit your systems to ensure ongoing compliance with CIS recommendations.
- Automation Tools: Consider using CIS-CAT (CIS Configuration Assessment Tool) or other automation tools to assess and enforce compliance across your infrastructure.
Benefits of CIS Compliance
- Standardized Security: Ensures that your organization follows industry-recognized security best practices.
- Risk Reduction: Helps in reducing the attack surface by implementing critical security controls.
- Compliance with Other Standards: CIS Controls and Benchmarks often overlap with other compliance frameworks like PCI-DSS, NIST, and ISO, making it easier to achieve multiple compliance goals simultaneously.
- Improved Incident Response: By implementing CIS Controls, organizations are better equipped to detect, respond to, and recover from security incidents.
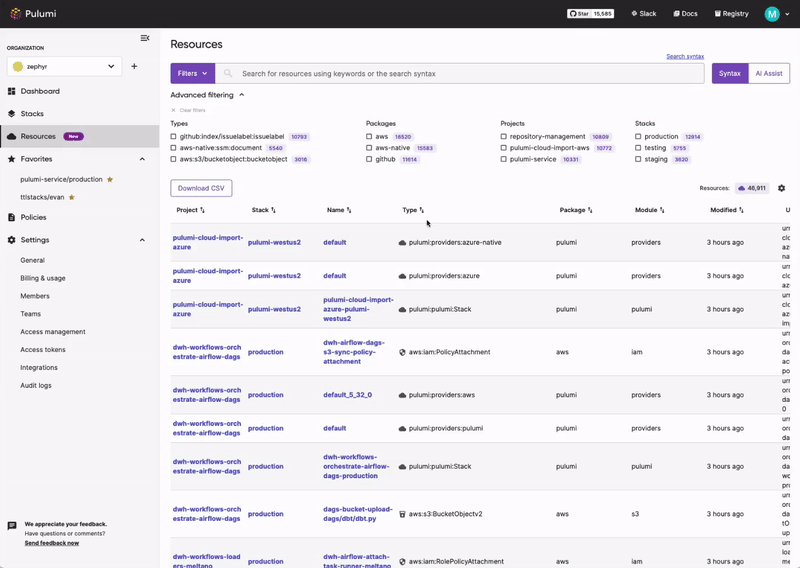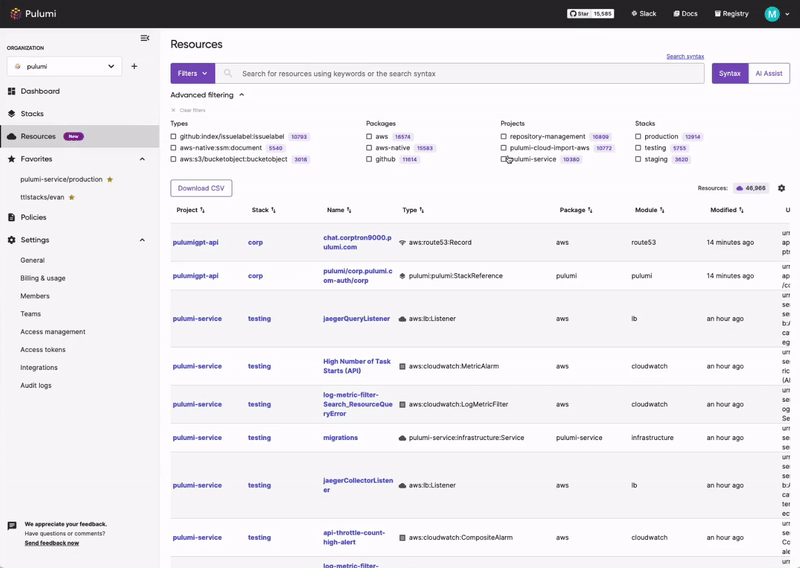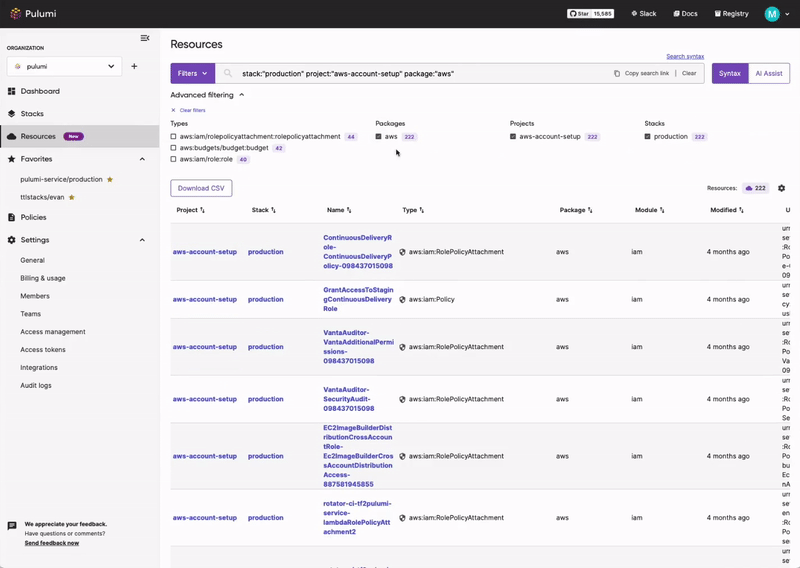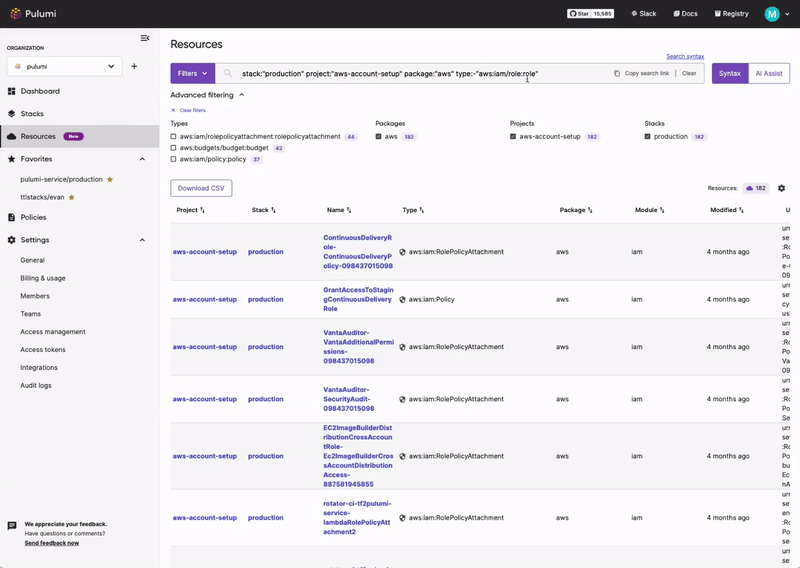
Pulumi Insights
Use Pulumi Insights to gain visibility into your cloud infrastructure's configuration to assess CIS compliance. Pulumi Insights is Intelligent Cloud Management. It helps you gain security, compliance, and cost insights into the entirety of your organization's cloud assets and automatically remediate issues.
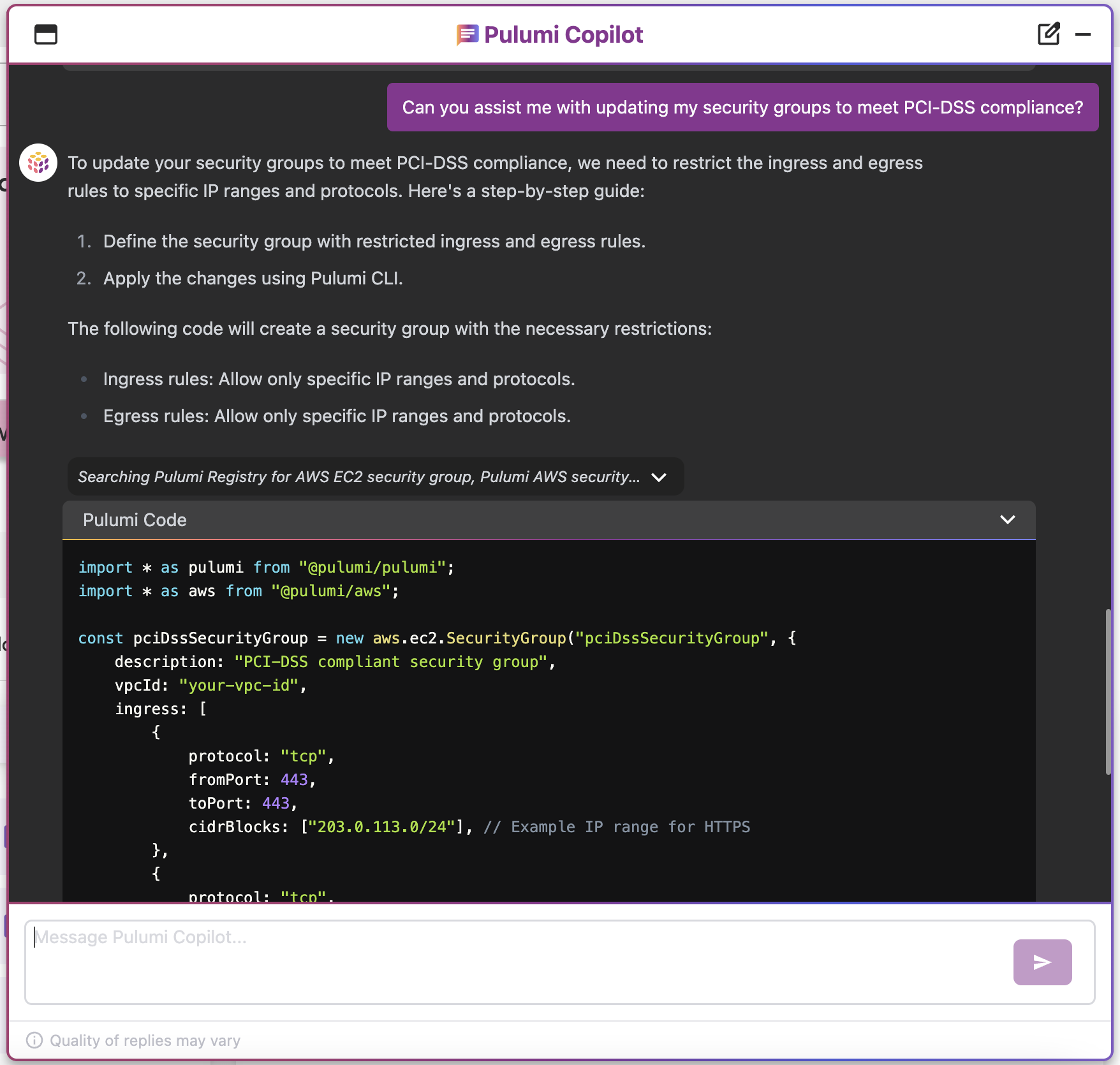
Pulumi Copilot
Use Pulumi Copilot to assist configuring your infrastructure to make it compliance ready. You can tap into the Pulumi Copilot's deep understanding of your organization's context to gain visibility into the configuration of resources and assess their compliance.
Compliance Ready Policies
With comprehensive coverage of Google Cloud, Pulumi Compliance Ready Policies provide an enhanced level of control and governance over your cloud resources. Pulumi Compliance Ready Policies empower you to enforce best practices, security standards, cost controls, and compliance requirements seamlessly within your infrastructure-as-code workflows.
What is Google Compute Engine?
Google Compute Engine provides scalable, high-performance virtual machines that run in Google's innovative data centers and worldwide fiber network. With a wide range of machine types, including predefined and custom options, users can optimize for compute, memory, or cost efficiency. Compute Engine offers features like live migration, automatic restart, and custom machine types, enabling users to run diverse workloads from micro-services to large-scale computational workloads.
What controls can I put in place to evaluate Google Compute Engine resources?
- Compute Engine disk snapshots should not be publicly restorable
- VPC default firewall rules should not allow inbound or outbound traffic
- Attached Compute Engine disks should be encrypted at rest
- Stopped Compute Engine instances should be removed after a specified time period
- Network security logging should be enabled for all VPCs
- Default encryption for Compute Engine disks should be enabled
- Compute Engine VMs should use Instance Metadata Service Version 2
- Compute Engine instances should not have a public IP address
- Compute Engine instances should be configured to use private VPC service connections
- Unused external IP addresses should be removed
- Firewall rules should not allow ingress from 0.0.0.0/0 to SSH port (22)
- Firewall rules should not allow ingress from 0.0.0.0/0 to RDP port (3389)
- VPCs should not automatically assign public IP addresses
- Unused firewall rules should be removed
- Compute Engine instances should not use multiple network interfaces (NICs)
- Firewall rules should only allow unrestricted incoming traffic for authorized ports
- Firewall rules should not allow unrestricted access to high-risk ports
- Both VPN tunnels for a Cloud VPN Gateway connection should be up
- Firewall rules should not allow ingress from 0.0.0.0/0 to port 22 or port 3389
- VPC peering connections should not automatically accept peering requests
- Compute Engine instances should not use legacy machine types
- Managed instance groups should not assign public IPs to NICs
- Compute Engine disks should be covered by a backup policy
- Cloud VPN Gateway connections should be labeled
- VPC route tables should be labeled
- Network Interfaces should be labeled
- Cloud VPN Gateways should be labeled
- External IP addresses should be labeled
- Compute Engine instances should be labeled
- Cloud NAT Gateways should be labeled
- Firewall rules should be labeled
- VPCs should be labeled
- VPC endpoint services should be labeled
- VPC flow logs should be labeled
- VPC peering connections should be labeled
- Cloud VPN Gateways should be labeled
- Client VPN endpoints should have client connection logging enabled
Speak to a Solutions Architect to implement policy as code to manage Compute Engine resources for CIS compliance.
Talk to a Solutions Architect
Get in touch with our Solutions Architects to get all your resources in use with Pulumi Insights