How to Achieve PCI DSS Compliance for AWS IAM
How to Achieve PCI DSS Compliance for AWS IAM
PCI DSS compliance is critical to protecting cardholder data that is processed, stored, and transmitted. Pulumi can assist you with making your AWS infrastructure PCI DSS compliant. Pulumi can help you identify existing cloud resources that are not in compliance, and it can also enforce compliance policies proactively before infrastructure is deployed. Get started with Pulumi to use these compliance tools or speak with a Solutions Architect to get an expert consultation.
What is PCI DSS Compliance?
PCI DSS (Payment Card Industry Data Security Standard) compliance refers to the adherence to a set of security standards designed to protect card information during and after a financial transaction. These standards are established by the Payment Card Industry Security Standards Council (PCI SSC), which was founded by major credit card companies like Visa, MasterCard, American Express, Discover, and JCB.
Key Aspects of PCI DSS Compliance
- Security Controls: Organizations must implement specific technical and operational security measures to safeguard cardholder data. This includes requirements like installing firewalls, encrypting cardholder data, and using antivirus software.
- Access Control: Only authorized personnel should have access to cardholder data. This involves setting up strong access control measures, such as unique user IDs and restricting physical access to sensitive data.
- Monitoring and Testing: Regularly monitor and test networks to ensure that security controls are functioning correctly and to identify vulnerabilities. This includes maintaining logs of all access to network resources and cardholder data.
- Information Security Policy: Organizations must maintain a policy that addresses information security for employees and contractors. This includes regular security awareness training.
- Regular Audits: Organizations that process, store, or transmit credit card information must undergo regular audits to ensure they are in compliance with PCI DSS requirements. This can involve self-assessment or external assessments, depending on the size of the organization and the volume of transactions processed.
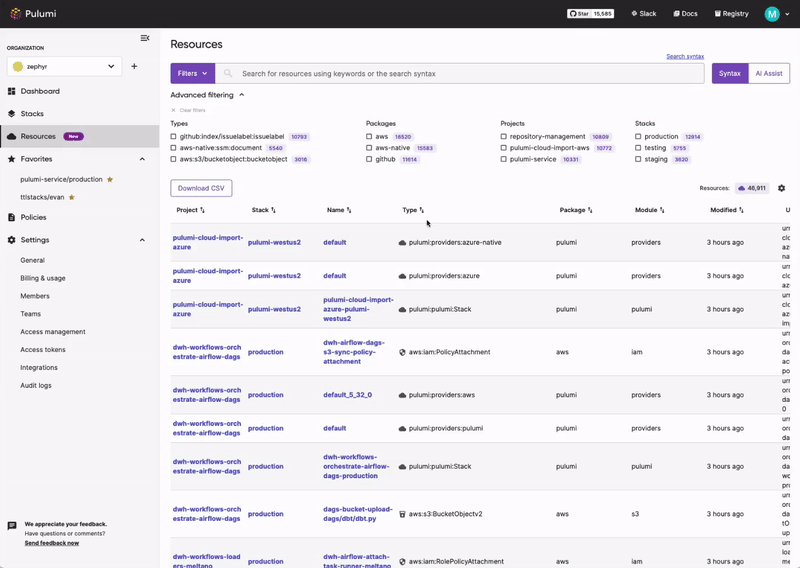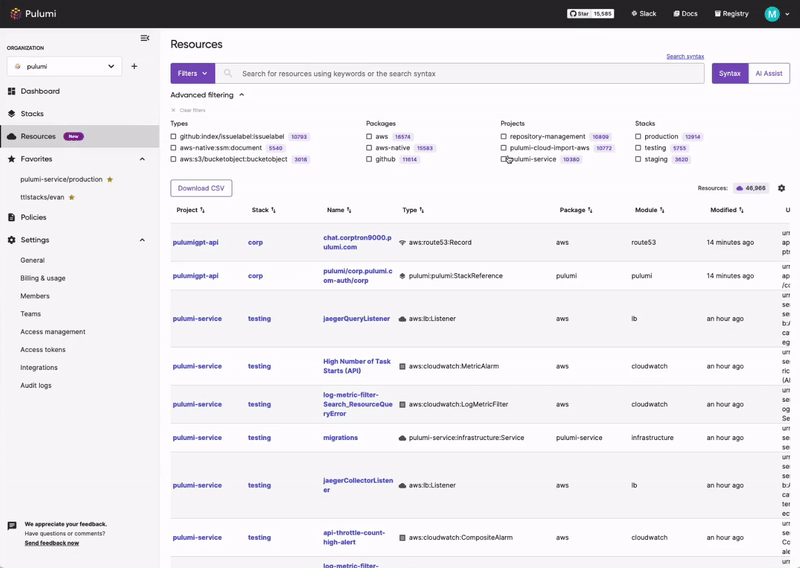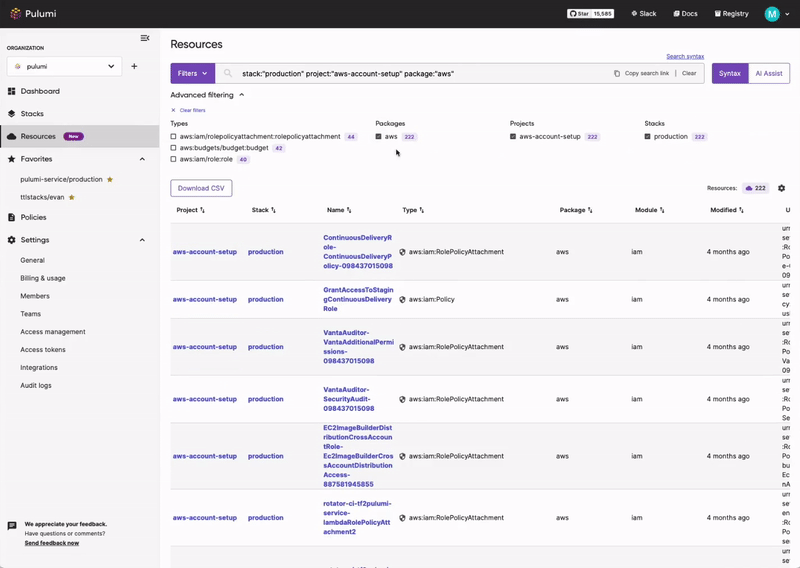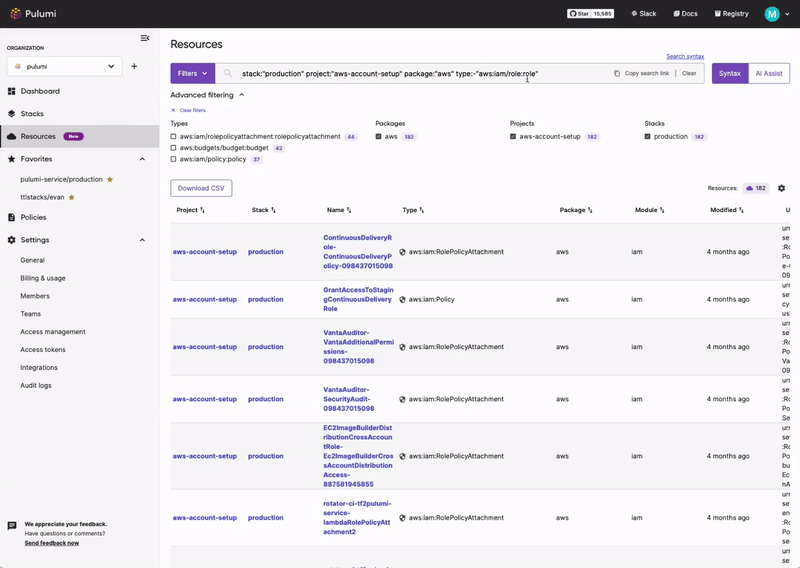
Pulumi Insights
Use Pulumi Insights to gain visibility into your cloud infrastructure's configuration to assess PCI DSS compliance. Pulumi Insights is Intelligent Cloud Management. It helps you gain security, compliance, and cost insights into the entirety of your organization's cloud assets and automatically remediate issues.
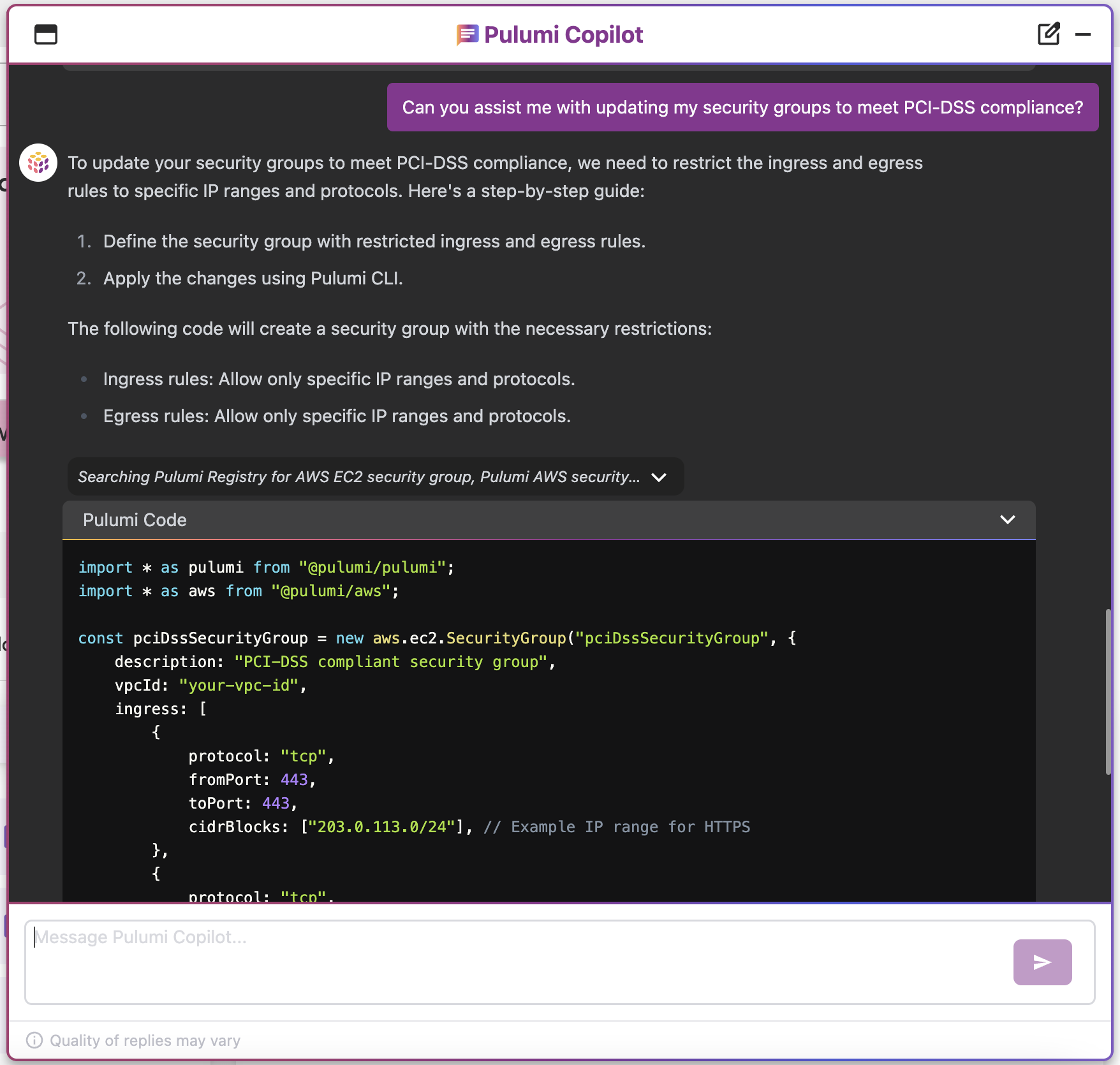
Pulumi Copilot
Use Pulumi Copilot to assist configuring your infrastructure to make it compliance ready. You can tap into the Pulumi Copilot's deep understanding of your organization's context to gain visibility into the configuration of resources and assess their compliance.
Compliance Ready Policies
With comprehensive coverage of AWS, Pulumi Compliance Ready Policies provide an enhanced level of control and governance over your cloud resources. Pulumi Compliance Ready Policies empower you to enforce best practices, security standards, cost controls, and compliance requirements seamlessly within your infrastructure-as-code workflows.
What is IAM Roles and Policies?
AWS IAM (Identity and Access Management) is a service that enables you to securely manage access to AWS resources. It allows you to create and control user permissions, defining who can access specific resources and under what conditions. IAM helps ensure security and compliance by enforcing fine-grained access controls across your AWS environment.
What controls can I put in place to evaluate IAM Roles and Policies resources?
- IAM policies should not allow full "*" administrative privileges
- IAM users should not have IAM policies attached
- IAM users' access keys should be rotated every 90 days or less
- IAM root user access key should not exist
- MFA should be enabled for all IAM users that have a console password
- Hardware MFA should be enabled for the root user
- Password policies for IAM users should have strong configurations
- Unused IAM user credentials should be removed
- MFA should be enabled for the root user
- Password policies for IAM users should have strong AWS Configurations
- Ensure IAM password policy requires at least one uppercase letter
- Ensure IAM password policy requires at least one lowercase letter
- Ensure IAM password policy requires at least one symbol
- Ensure IAM password policy requires at least one number
- Ensure IAM password policy requires minimum password length of 14 or greater
- Ensure IAM password policy prevents password reuse
- Ensure IAM password policy expires passwords within 90 days or less
- Ensure a support role has been created to manage incidents with AWS Support
- MFA should be enabled for all IAM users
- IAM customer managed policies that you create should not allow wildcard actions for services
- IAM user credentials unused for 45 days should be removed
- IAM Access Analyzer analyzers should be tagged
- IAM roles should be tagged
- IAM users should be tagged
- Expired SSL/TLS certificates managed in IAM should be removed
- IAM identities should not have the AWSCloudShellFullAccess policy attached
- IAM Access Analyzer external access analyzer should be enabled
Speak to a Solutions Architect to implement policy as code to manage IAM resources for PCI DSS compliance.
Talk to a Solutions Architect
Get in touch with our Solutions Architects to get all your resources in use with Pulumi Insights