Managing credentials with Open ID Connect for Pulumi Deployments
Posted on
After launching Pulumi Deployments a few months ago and receiving a ton of community feedback (thank you!) today we are launching an integration with OpenID Connect (OIDC) to enable temporary credentials and granular access controls. We would like to thank GitHub user eriklz for creating the original request for this functionality.
OpenID Connect (OIDC) is an identity layer built on top of the OAuth 2.0 framework. It allows third-party applications to verify the identity of the end-user and to obtain basic user profile information. OIDC uses JSON web tokens (JWTs), which you can obtain using flows conforming to the OAuth 2.0 specifications.
Overview
The main benefits of using the OIDC integration for Pulumi Deployments are as follows:
- Temporary credentials: You can move away from long term credentials within your organization to leverage temporary credentials that are generated every time a deployment runs. The Pulumi Service issues a new OIDC token that is limited to that deployment. This token is used to obtain cloud credentials that automatically expire, meaning you do not need to store sensitive credentials that are reused with each deployment.
- Granular access control: The OIDC token generated by the Pulumi Service contains detailed information about the deployment with which it is associated. In AWS for example, you can configure our OIDC integration to only use temporary credentials if that token is associated with a particular Pulumi stack or Pulumi organization. This enables you to follow the principle of least privilege access and scope access down to only what is needed. For AWS, Azure, and GCP, Pulumi Deployments can automatically exchange its OIDC token for temporary credentials and make those credentials available to providers. For advanced scenarios or other cloud providers, the OIDC token can be manually exchanged for credentials by the user.
Setup
Calling the Deployments REST API
You can call the Deployments REST API and use OIDC instead of cloud secrets. Here is an example of how that might look:
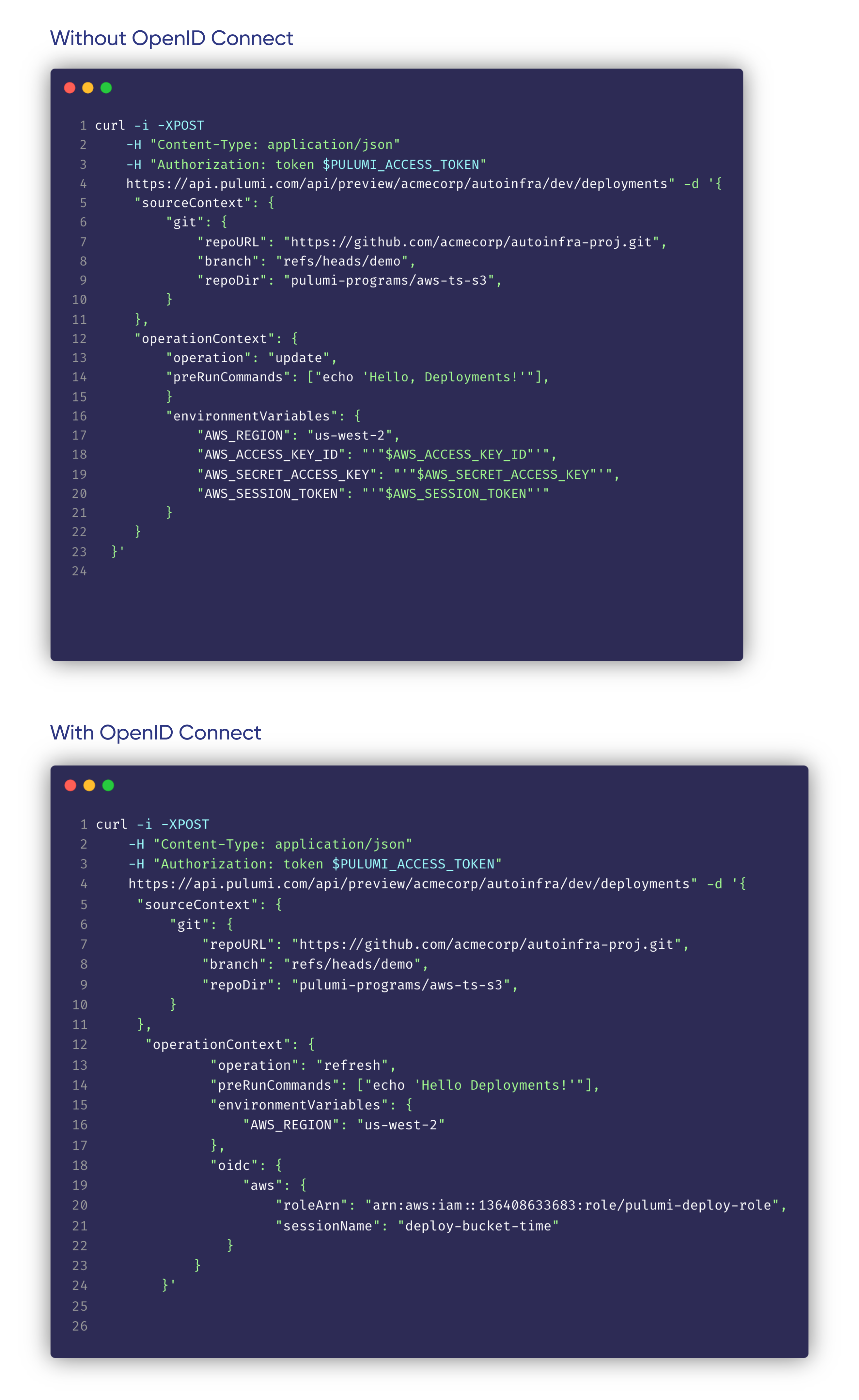
Enabling OIDC for your Stack for Git Push to Deploy
In order to use the Git Push to Deploy and Click to Deploy features in the Pulumi Service console you will need to enable OIDC for your stack in the console. In order to enable it you will need to be an admin of your Pulumi organization.
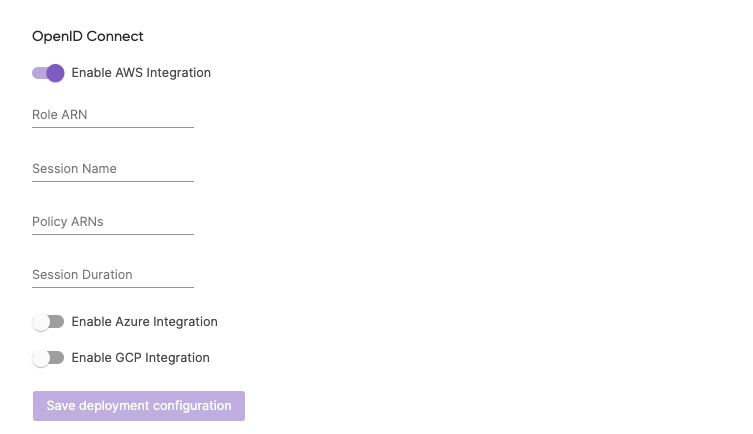
- Navigate to your stack in the Pulumi Console.
- Open the stack’s “Settings” tab.
- Choose the “Deploy” panel.
- Under the “OpenID Connect” header, toggle to your cloud provider
- Follow the cloud provider specific docs below
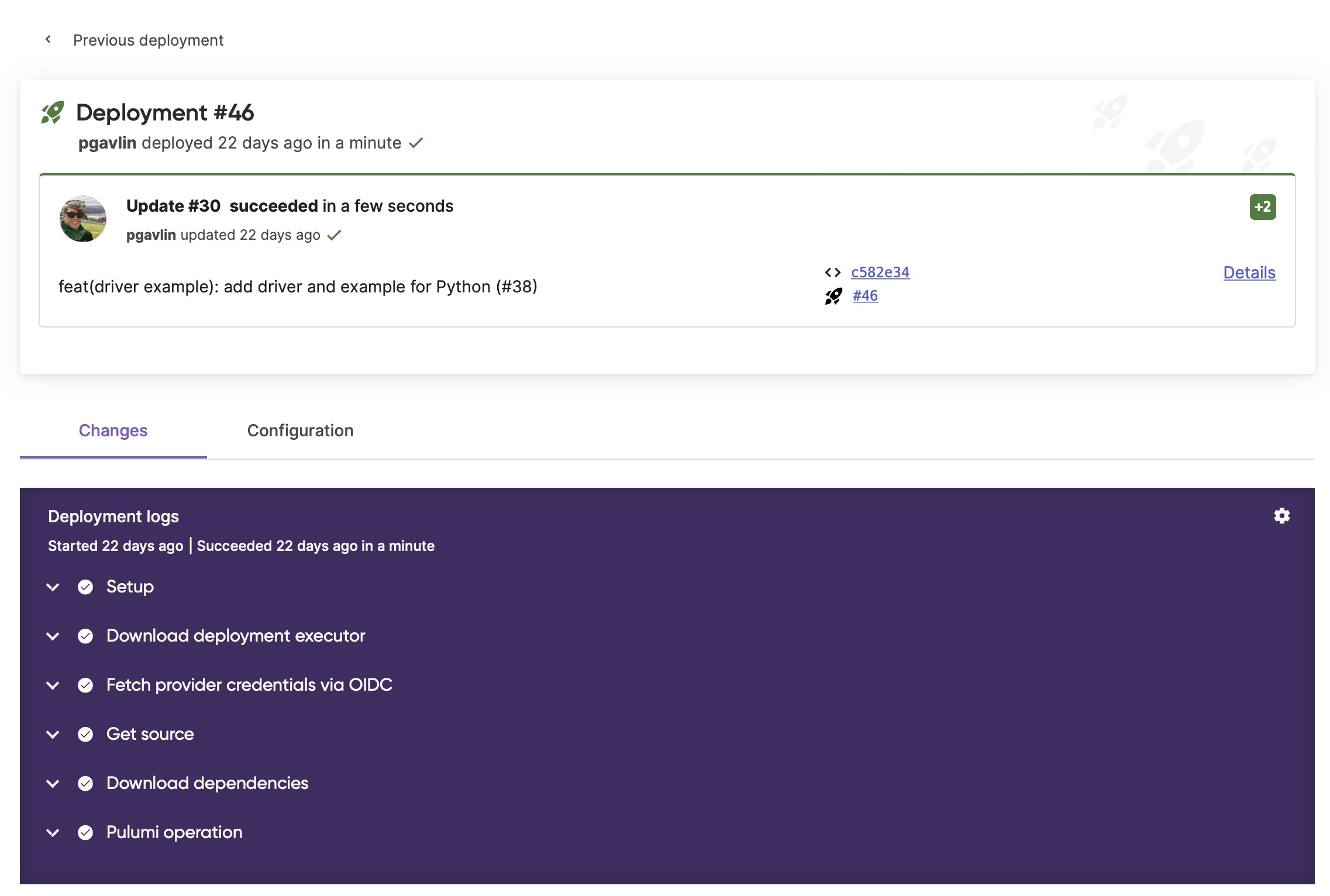
Viewing Deployment logs
Once OIDC is set up you will see a new step in your Deployment logs “Fetch credentials via OIDC”
Getting access to Pulumi Deployments
Pulumi Deployments is available in preview today. Deployments are free during the preview, with usage-based pricing to come. Check out these resources to get started today:
- Request access to the Pulumi Deployments preview
- Pulumi Deployments examples repo
- Pulumi Deployments documentation
- Pulumi Deployments REST API documentation
- Automation API examples
Please submit an issue in the Pulumi Service Requests repo if you have feature requests for the Pulumi Service or join our Slack channel(#pulumi-deployments) if you have questions.
🚀🚀🚀 Happy building! 🚀🚀🚀

