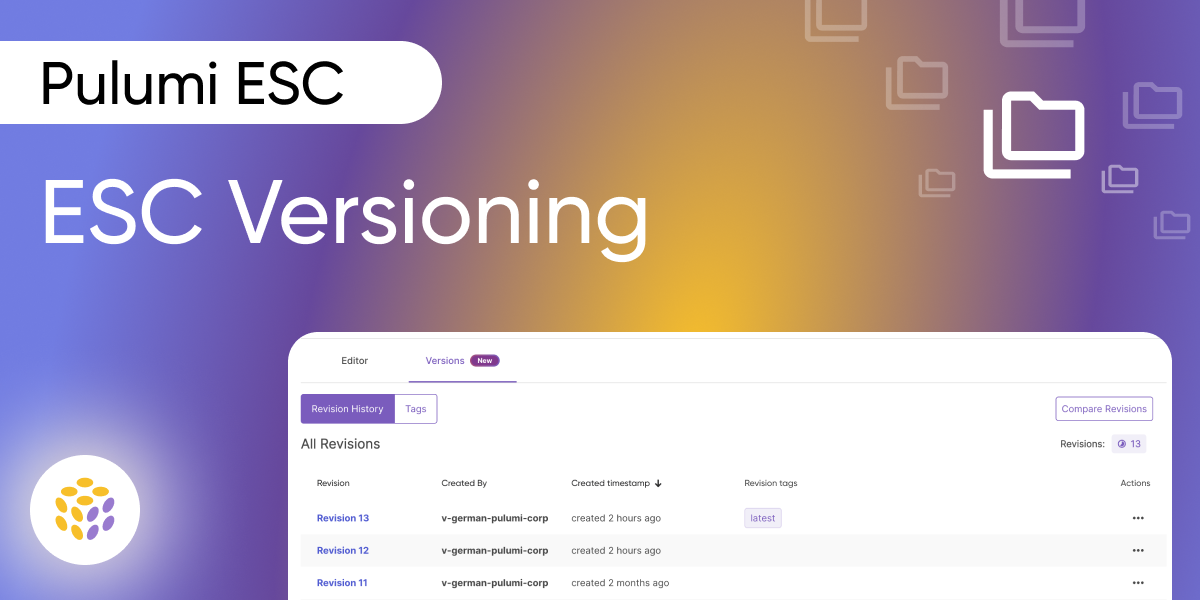
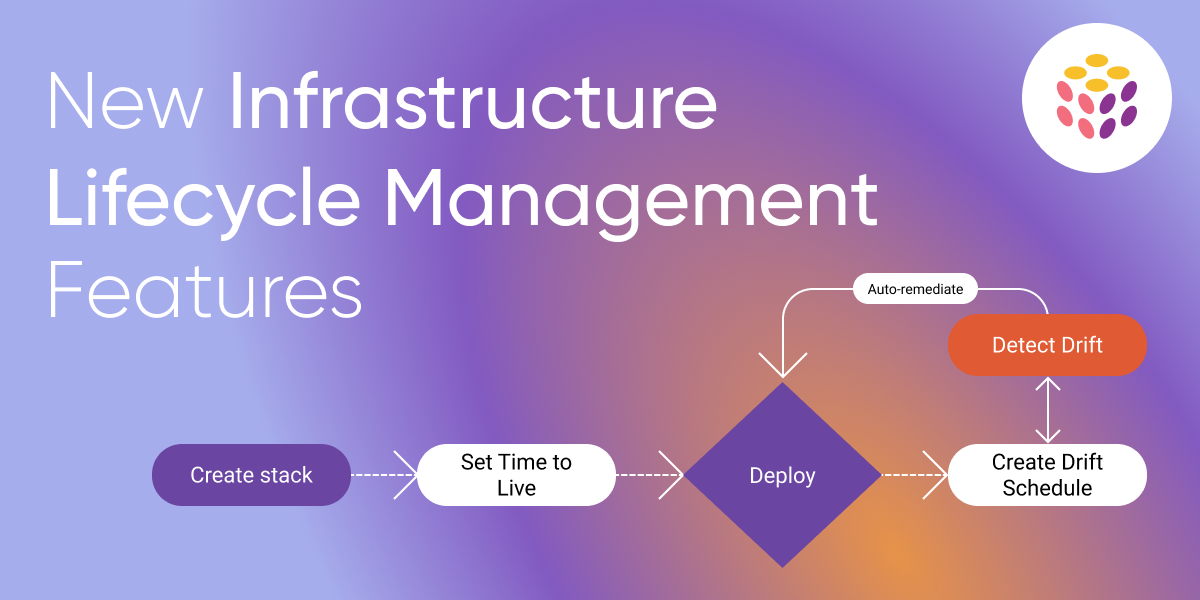
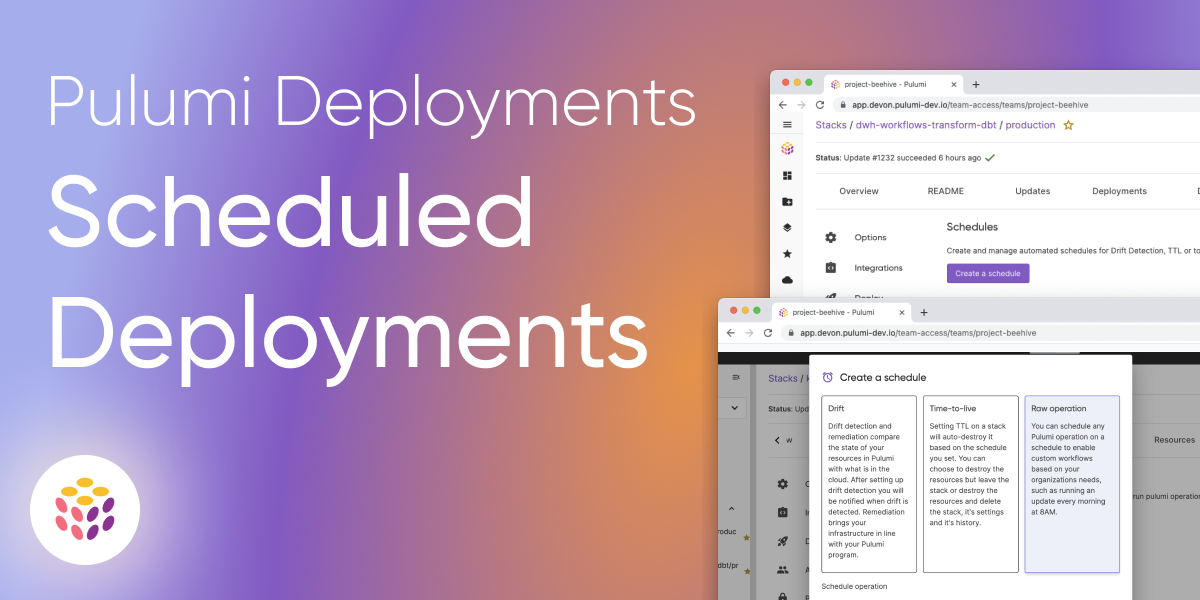
Introducing Resource Transforms: Enhancing Flexibility for Packaged Component Resources

Pulumi has supported a Transformations system for a number of years now. This has proved to be a powerful and flexible escape hatch for modifying resource properties and options across your entire program. For example, you could use Transformations to automatically apply tags to all taggable resources in your program, including the children of component resources.
However, there is one major limitation with the existing Transformations system: it isn’t able to transform the children of packaged component resources, such as those in awsx and eks. This limitation is due to the fact that packaged component resources are created in a separate provider process and Transformations only work with resources created in your program’s process.
To address this limitation we’re introducing a new system called Transforms, which works with all resources, including packaged component resources and their children. The new Transforms system is intended to fully replace the old Transformations system (we plan to deprecate the old system in the future).