This post is part 3 in a series on the Kubernetes API. Earlier,
Part 1
focused on the lifecycle of a Pod, and later
Part 3
details how Kubernetes deployments work.
Why isn’t my Pod getting any traffic?
An experienced ops team running on GKE might assemble the following
checklist to help answer this question:
- Does a
Service exist? Does that service have a .spec.selector
that matches some number of Pods? - Are the
Pods alive and has their readiness probe passed? - Did the
Service create an Endpoints object that specifies one or
more Pods to direct traffic to? - Is the
Service reachable via DNS? When you kubectl ``exec into a
Pod and you use curl to poke the Service hostname, do you get
a response? (If not, does any Service have a DNS entry?) - Is the
Service reachable via IP? When you SSH into a Node and
you use curl to poke the Service IP, do you get a response? - Is
kube-proxy up? Is it writing iptables rules? Is it proxying to
the Service?
This question might have the highest complexity-to-sentence-length ratio
of any question in the Kubernetes ecosystem. Unfortunately, it’s also a
question that every user finds themselves asking at some point. And
when they do, it usually means their app is down.
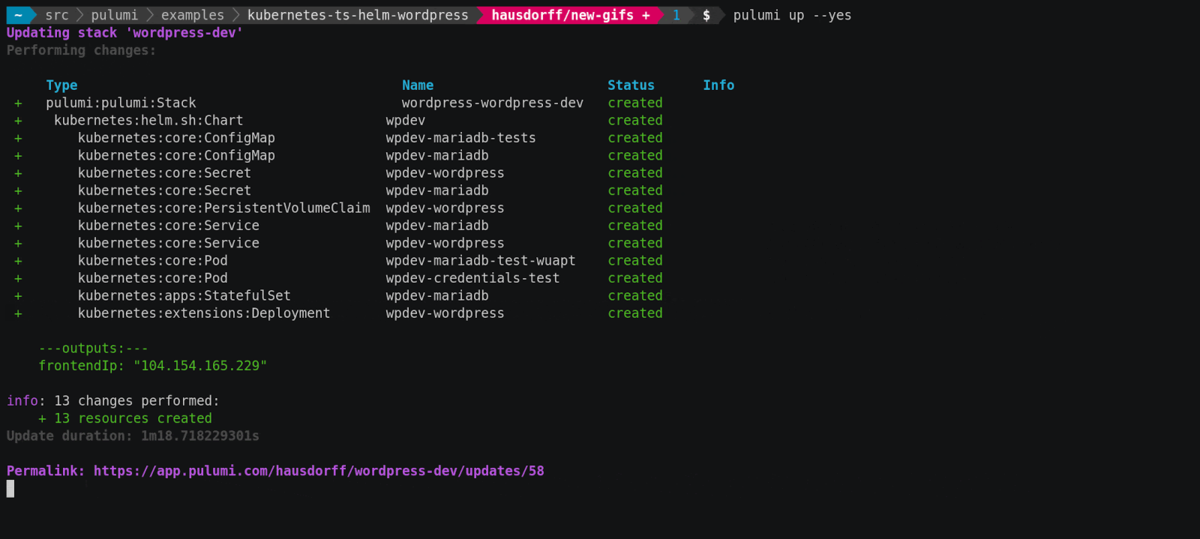
To help answer questions like this, we’ve been developing a small
diagnostic tool, kubespy. In this post we’ll look at the new
kubespy trace command, which is broadly aimed at automating questions
1, 2, 3, and providing “hints” about 4 and 5.
Read more →